Being paranoid about user enumeration attack using Devise gem in Rails apps
Use Devise's in built paranoid mode to solve user renumeration attacks.
I have used devise for authentication in all my Rails projects in last 7 years. But recently I came across a nifty feature provided by Devise – paranoid mode.
In our Rails application, we have ability to reset password by clicking on the "Forgot password" link using devise. If we enter user's email, we will get an error if the user is not present in the database.
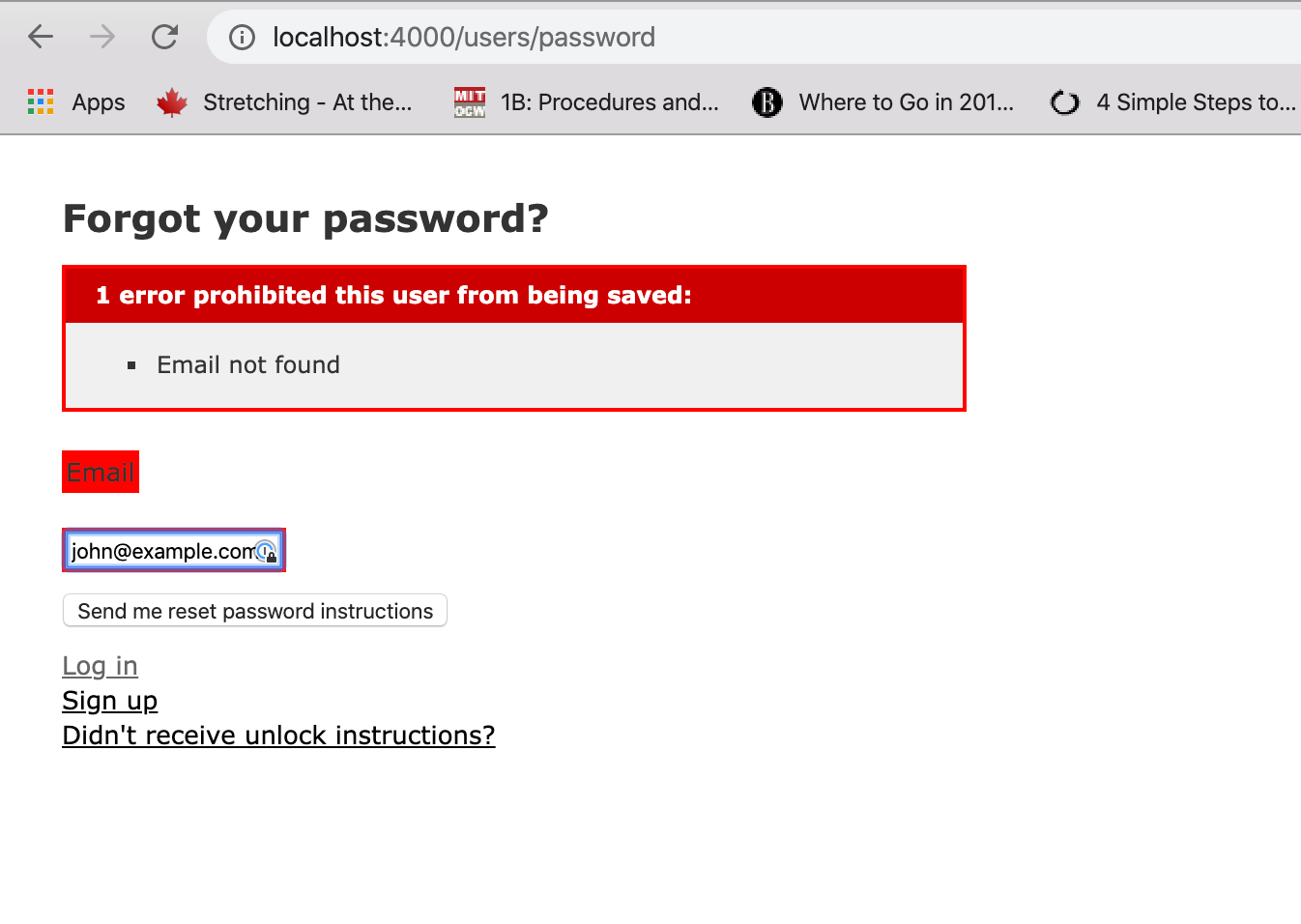
But this message indicates that user with given email does not exist in database. One can keep trying with different email addresses to see which ones exist in database and which ones don't.
This is called user enumeration attack and is one of the top web attacks listed in OWASP https://www.owasp.org/index.php/Testing_for_User_Enumeration_and_Guessable_User_Account_(OWASP-AT-002)
Devise solves this problem by providing paranoid mode.
Devise.setup do |config|
config.paranoid = true
endOnce we enable the paranoid mode as above, Devise does not reveal whether the user exists in the database or not. This mitigates the problem of user enumeration in a way.
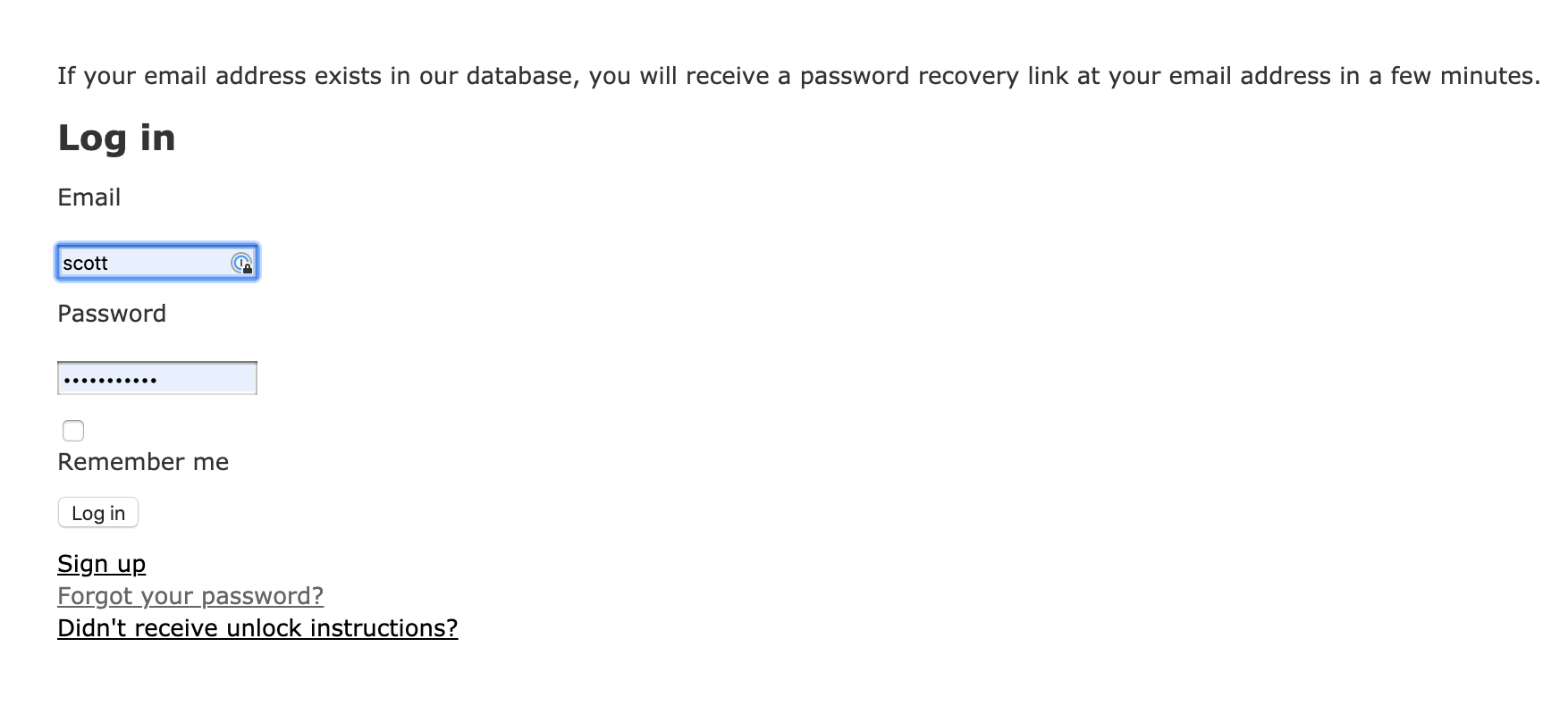
Paranoid mode is not applicable when we are creating a new user. Because in that case, we do want to show an error that user with given email already exists.
Paranoid mode is not available in registrable module, only available in confirmable, revokable and unlockable modules.
It is not a full proof way of stopping the user remuneration attack but it helps in mitigating it in a way.
There is also another school of thought which discourages use of the paranoid mode and instead suggests using 2FA and Rack attack. You can read about it here. Thanks to janko-m for suggesting it on reddit.
Interested in knowing more how I use Rails in day to day work? Subscribe to my newsletter.
