External Blog Posts
Here are some of the blog posts I have written for external publications.
On Last9 Blog —
Understanding Metrics, Events, Logs and Traces - Key Pillars of Observability
Understanding Metrics, Logs, Events and Traces - the key pillars of observability and their pros and cons for SRE and DevOps teams.
 Book a DemoStart for FreeBook a Demo
Book a DemoStart for FreeBook a Demo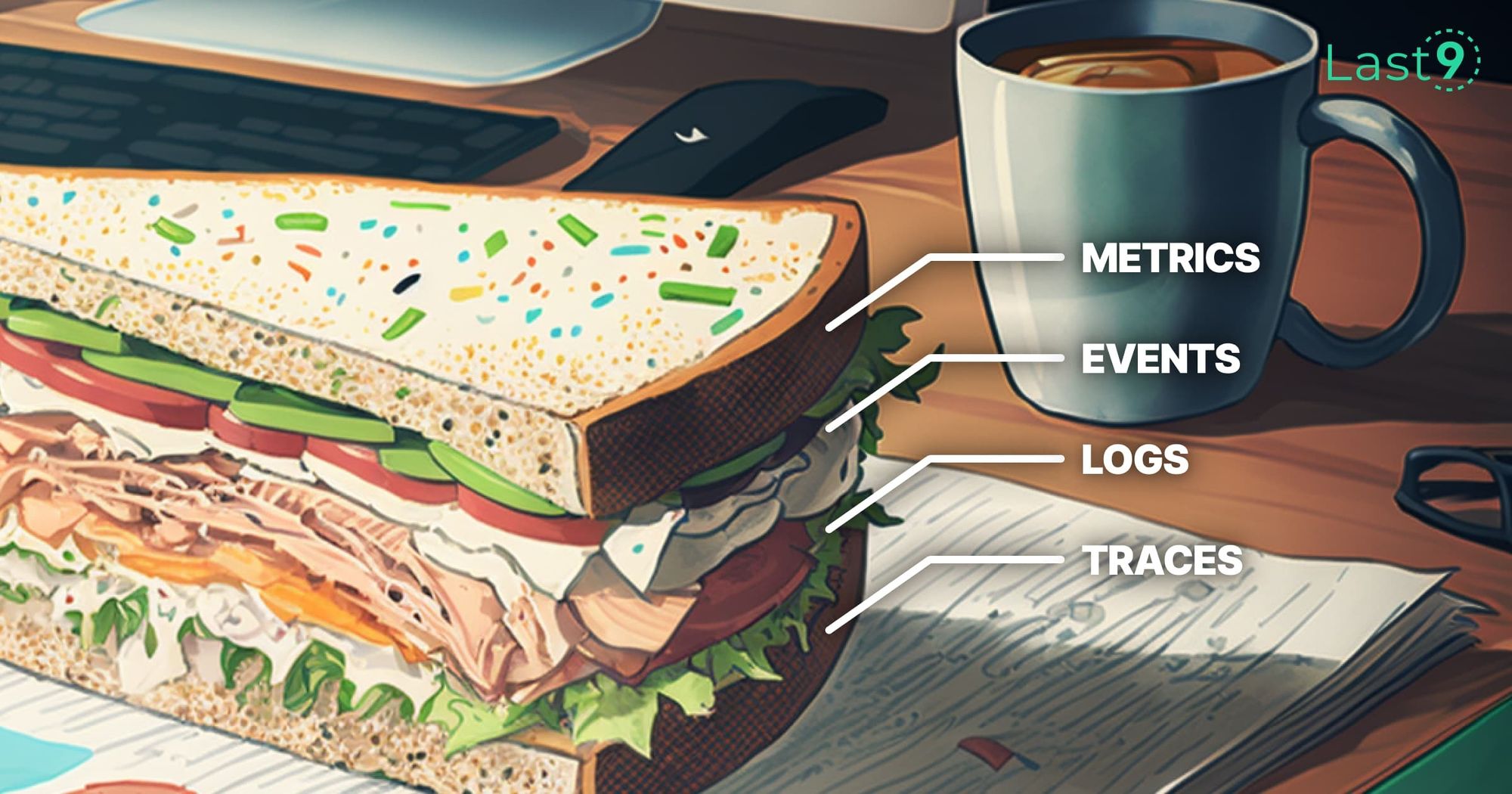
Filtering Metrics by Labels in OpenTelemetry Collector
How to filter metrics by labels using OpenTelemetry Collector
 Book a DemoGet Started
Book a DemoGet Started
A practical guide for implementing SLO
How to set Service Level Objectives with 3 steps guide
 Book a DemoGet Started
Book a DemoGet Started
How to Improve On-Call Experience!
Better practices and tools for management of on-call practices
 Book a DemoGet Started
Book a DemoGet Started
Monorepos - The Good, Bad, and Ugly
A monorepo is a single version control repository that holds all the code,configuration files, and components required for your project (includingservices like search) and it’s how most projects start. However, as a projectgrows, there is debate as to whether the project’s code should be split in…
 Book a DemoGet Started
Book a DemoGet Started
Prometheus vs InfluxDB | Last9
What are the differences between Prometheus and InfluxDB - use cases, challenges, advantages and how you should go about choosing the right tsdb
 Book a DemoStart for Free
Book a DemoStart for Free
What is Prometheus Remote Write | Last9
Learn about what is Prometheus Remote Write and how to configure it.
 Book a DemoStart for FreeLast9 Documentation
Book a DemoStart for FreeLast9 Documentation
OpenTelemetry vs. Prometheus | Last9
OpenTelemetry vs. Prometheus - Difference in architecture, and metrics
 Book a DemoStart for Free
Book a DemoStart for Free
SRE vs Platform Engineering | Last9
What’s the difference between SREs and Platform Engineers? How do they differ in their daily tasks?
 Book a DemoStart for Free
Book a DemoStart for Free
Downsampling & Aggregating Metrics in Prometheus: Practical Strategies to Manage Cardinality and Query Performance | Last9
A comprehensive guide to downsampling metrics data in Prometheus with alternate robust solutions
 Book a DemoStart for Free
Book a DemoStart for Free
The difference between DevOps, SRE, and Platform Engineering | Last9
In reliability engineering, three concepts keep getting talked about - DevOps, SRE and Platform Engineering. How do they differ?
 Book a DemoStart for Free
Book a DemoStart for Free
Mastering Prometheus Relabeling: A Comprehensive Guide | Last9
A comprehensive guide to relabeling strategies in Prometheus
 Book a DemoStart for Free
Book a DemoStart for Free
OpenTelemetry vs. OpenTracing | Last9
OpenTelemetry vs. OpenTracing - differences, evolution, and ways to migrate to OpenTelemetry
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus vs Thanos | Last9
Everything you want to know about Prometheus and Thanos, their differences, and how they can work together.
 Book a DemoStart for Free
Book a DemoStart for Free
What is OpenTelemetry Collector | Last9
What is OpenTelemetry Collector, Architecture, Deployment and Getting started
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus Alternatives | Last9
What are the alternatives to Prometheus? A guide to comparing different Prometheus Alternatives.
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus Operator Guide | Last9
What is Prometheus Operator, how it can be used to deploy Prometheus Stack in Kubernetes environment
 Book a DemoStart for Free
Book a DemoStart for Free
How to Manage High Cardinality Metrics in Prometheus | Last9
A comprehensive guide on understanding high cardinality Prometheus metrics, proven ways to find high cardinality metrics and manage them.
 Book a DemoStart for FreeBook a Demo
Book a DemoStart for FreeBook a Demo
Best Practices Using and Writing Prometheus Exporters | Last9
This article will go over what Prometheus exporters are, how to properly find and utilize prebuilt exporters, and tips, examples, and considerations when building your own exporters.
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus Federation ⏤ Scaling Prometheus Guide | Last9
We discuss the nuances of Federation in Prometheus, address Prometheus Scaling Challenges along with alternatives to Prometheus federation
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus Metrics Types - A Deep Dive | Last9
A deep dive on different metric types in Prometheus and best practices
 Book a DemoStart for Free
Book a DemoStart for Free
How to Instrument Java Applications using OpenTelemetry - Tutorial & Best Practices | Last9
A comprehensive guide to instrument Java applications using OpenTelemetry libraries
 Book a DemoStart for Free
Book a DemoStart for Free
How To Instrument Golang app using OpenTelemetry - Tutorial & Best Practices | Last9
A comprehensive guide to instrument Golang applications using OpenTelemetry libraries for metrics and traces
 Book a DemoStart for Free
Book a DemoStart for Free
Prometheus and Grafana | Last9
What is Prometheus and Grafana, What is Prometheus and Grafana used for, What is difference between Prometheus and Grafana.
 Book a DemoStart for Free
Book a DemoStart for Free
SRECon EMEA 2024 - Day 3 | Last9
Here’s a snapshot of the key talks, important ideas, and memorable moments that set the stage for SRECon EMEA Dublin 2024!
 We hope you've been keeping up with our Day 1 and Day 2 updates! If you happened to miss them, you can catch the highlights here.Day 1 Highlights!SRECon EMEA 2024 - Day 1 | Last9Here’s a quick rundown of the standout talks, big ideas, and memorable moments that kicked things off in SRECon EMEA Dublin 2024!Last9Day 2 Highlights!SRECon EMEA 2024 - Day 2 | Last9Here’s a quick recap of the standout talks, key insights, and unforgettable moments that got things rolling at SRECon EMEA Dublin 2024!Last9Highlights from Day 3Here are a few sessions that really sparked some great conversations and that I personally enjoyed:Riot Games: Evolution of Observability at the Gaming CompanyErick and Kirill from Riot Games walked us through how they’re improving observability to keep up with the fast-growing gaming world. With gaming expected to double in the next decade, Riot is focused on keeping gameplay stable and smooth, especially for competitive online players. It was refreshing to hear their take and know more about observability in gaming.A Powerful Logs Management Solution We All Have and Use but We Underestimate: systemd-journalCosta from Netdata talked about the exciting but often overlooked features of systemd-journal. He shared some relatable examples that showed how to transform basic logs into structured entries, making it clear why this tool can be so useful for the SRE community.Blast Radius Reduction for Large-Scale Distributed SystemsI found this one intriguing! Linhua from the Huawei Ireland Research Centre discussed the challenges of building large-scale distributed systems. He emphasized the 'design for failure' approach and shared some strategies to reduce the impact of failures.Linhua also stressed how crucial it is to verify designs for reliability and the importance of smart planning to maintain stability in complex systems.Building New SRE TeamsAvleen and Stephane hosted a relaxed session on building new SRE teams. It was a great chance to connect with other SREs and hear about their experiences—something I also love doing with my SREStories!Even if you can’t be there in person — keep an eye out for the decks and recordings—they’re going to be well worth a watch.Prathamesh at Last9 boothAnd that’s a wrap for SRECon EMEA 2024! It was an incredible few days of learning and connecting. A huge thanks to the organizers, speakers, and sponsors for making it such a memorable event!Subscribe
We hope you've been keeping up with our Day 1 and Day 2 updates! If you happened to miss them, you can catch the highlights here.Day 1 Highlights!SRECon EMEA 2024 - Day 1 | Last9Here’s a quick rundown of the standout talks, big ideas, and memorable moments that kicked things off in SRECon EMEA Dublin 2024!Last9Day 2 Highlights!SRECon EMEA 2024 - Day 2 | Last9Here’s a quick recap of the standout talks, key insights, and unforgettable moments that got things rolling at SRECon EMEA Dublin 2024!Last9Highlights from Day 3Here are a few sessions that really sparked some great conversations and that I personally enjoyed:Riot Games: Evolution of Observability at the Gaming CompanyErick and Kirill from Riot Games walked us through how they’re improving observability to keep up with the fast-growing gaming world. With gaming expected to double in the next decade, Riot is focused on keeping gameplay stable and smooth, especially for competitive online players. It was refreshing to hear their take and know more about observability in gaming.A Powerful Logs Management Solution We All Have and Use but We Underestimate: systemd-journalCosta from Netdata talked about the exciting but often overlooked features of systemd-journal. He shared some relatable examples that showed how to transform basic logs into structured entries, making it clear why this tool can be so useful for the SRE community.Blast Radius Reduction for Large-Scale Distributed SystemsI found this one intriguing! Linhua from the Huawei Ireland Research Centre discussed the challenges of building large-scale distributed systems. He emphasized the 'design for failure' approach and shared some strategies to reduce the impact of failures.Linhua also stressed how crucial it is to verify designs for reliability and the importance of smart planning to maintain stability in complex systems.Building New SRE TeamsAvleen and Stephane hosted a relaxed session on building new SRE teams. It was a great chance to connect with other SREs and hear about their experiences—something I also love doing with my SREStories!Even if you can’t be there in person — keep an eye out for the decks and recordings—they’re going to be well worth a watch.Prathamesh at Last9 boothAnd that’s a wrap for SRECon EMEA 2024! It was an incredible few days of learning and connecting. A huge thanks to the organizers, speakers, and sponsors for making it such a memorable event!Subscribe
SRECon EMEA 2024 - Day 2 | Last9
Here’s a quick recap of the standout talks, key insights, and unforgettable moments that got things rolling at SRECon EMEA Dublin 2024!
 Hopefully, you’ve caught our updates from Day 1 at SRECon. If you missed it, you can still check out the highlights here.Now, let’s jump into what stood out on Day 2 of SRECon 2024!Highlights from Day 2:Here's a quick recap of the sessions that sparked conversations on Day 2:Treat Your Code as a Crime SceneThe session started with a quick and engaging look at offender profiling, and then we explored how those ideas can be applied to software development. We got an idea of how version-control data, which is often just sitting there, can reveal interesting behaviors and patterns within a development team.Finding the Capacity to Grieve Once MoreAlexandros shared some fascinating stories from Wikipedia's experience with unexpected traffic spikes, particularly during significant events like notable deaths, which can sometimes cause serious outages. He talked about how they thought they had tackled these challenges, only to face a major outage in 2020 caused by a tragic loss and a DDoS attack.Anomaly Detection in Time Series from Scratch Using Statistical AnalysisIvan Shubin shared his insights on tackling the tricky world of anomaly detection in time series data. He made a compelling case that you don't need AI or machine learning to get good results. He showcased how basic statistical methods can do the job effectively. SRE in Small OrgsDuring this session, Emil and Joan invited everyone to join a casual conversation about the ins and outs of running SRE teams in smaller organizations. It was all about connecting with others in similar situations and bouncing around ideas together.Monitoring and AlertingDaria and Niall had a laid-back conversation with attendees about monitoring and alerting, followed by a fun Q&A session. It was really interesting to hear how SREs think about monitoring and alerting!Synthetic Monitoring and E2E Testing: 2 Sides of the Same CoinCarly delivered an insightful session on the relationship between Synthetic Monitoring and E2E Testing. She addressed the cultural and tooling challenges that keep development and SRE teams in silos, even in a DevOps environment.How Snowflake Migrated All Alerts and Dashboards to a Prometheus-Based Metrics System in 3 MonthsIn his talk, Carlos Mendizabal took the audience through Snowflake's journey of migrating all alerts and dashboards to a Prometheus-based metrics system in just three months. He shared the ups and downs of rewriting every single alert and dashboard for system monitoring.If you missed out on our amazing merch yesterday track us down and grab yours! 😎I am already looking forward to Day 3 of SRECon Dublin 2024.Subscribe
Hopefully, you’ve caught our updates from Day 1 at SRECon. If you missed it, you can still check out the highlights here.Now, let’s jump into what stood out on Day 2 of SRECon 2024!Highlights from Day 2:Here's a quick recap of the sessions that sparked conversations on Day 2:Treat Your Code as a Crime SceneThe session started with a quick and engaging look at offender profiling, and then we explored how those ideas can be applied to software development. We got an idea of how version-control data, which is often just sitting there, can reveal interesting behaviors and patterns within a development team.Finding the Capacity to Grieve Once MoreAlexandros shared some fascinating stories from Wikipedia's experience with unexpected traffic spikes, particularly during significant events like notable deaths, which can sometimes cause serious outages. He talked about how they thought they had tackled these challenges, only to face a major outage in 2020 caused by a tragic loss and a DDoS attack.Anomaly Detection in Time Series from Scratch Using Statistical AnalysisIvan Shubin shared his insights on tackling the tricky world of anomaly detection in time series data. He made a compelling case that you don't need AI or machine learning to get good results. He showcased how basic statistical methods can do the job effectively. SRE in Small OrgsDuring this session, Emil and Joan invited everyone to join a casual conversation about the ins and outs of running SRE teams in smaller organizations. It was all about connecting with others in similar situations and bouncing around ideas together.Monitoring and AlertingDaria and Niall had a laid-back conversation with attendees about monitoring and alerting, followed by a fun Q&A session. It was really interesting to hear how SREs think about monitoring and alerting!Synthetic Monitoring and E2E Testing: 2 Sides of the Same CoinCarly delivered an insightful session on the relationship between Synthetic Monitoring and E2E Testing. She addressed the cultural and tooling challenges that keep development and SRE teams in silos, even in a DevOps environment.How Snowflake Migrated All Alerts and Dashboards to a Prometheus-Based Metrics System in 3 MonthsIn his talk, Carlos Mendizabal took the audience through Snowflake's journey of migrating all alerts and dashboards to a Prometheus-based metrics system in just three months. He shared the ups and downs of rewriting every single alert and dashboard for system monitoring.If you missed out on our amazing merch yesterday track us down and grab yours! 😎I am already looking forward to Day 3 of SRECon Dublin 2024.Subscribe
SRECon EMEA 2024 - Day 1 | Last9
Here’s a quick rundown of the standout talks, big ideas, and memorable moments that kicked things off in SRECon EMEA Dublin 2024!
 If you’re an SRE—or know and love one—then you probably already know SRECon is the annual meetup for site reliability engineers.So, What’s SRECon All About?Hosted by USENIX, SRECon brings together everyone from newbies to industry legends, all eager to talk about what works, what fails spectacularly, and how we can keep pushing for more reliable, scalable tech. It’s a community-driven, solutions-oriented conference for anyone looking to up their reliability game.SRECon Dublin 2024New for 2024: The Discussion TrackThis year, SRECon introduced a fresh concept: the Discussion Track. It’s a space where attendees can go beyond presentations and have interactive discussions, led by experienced hosts who shape each session into whatever the group needs: an AMA, casual brainstorming, or an unconference vibe. Highlights from Day 1Here are some of the talks I enjoyed at SRECon Dublin 2024:Dude, You Forgot the Feedback: How Your Open Loop Control Planes Are Causing OutagesThe title alone brought people in. This session highlighted the risks of "fire and forget" control planes that lack real-time feedback, which can lead to outages. Laura walked through ways to design control planes that actively report on actions and their impacts, making systems more reliable and reducing operational errors.SRE Saga: The Song of Heroes and VillainsThis talk shared some great practical examples to help SRE teams build resilience and work better together when facing challenges. It also explored fun ways to tap into that "superhero" energy within the team, encouraging talent development while keeping everyone on the same page and accountable.The Frontiers of Reliability EngineeringThe discussion focused on three key frontiers they actively invested in: Data Operations and Monitoring Event-Based Systems, Mobile Observability, and Effective Management Practices for Reliability.Heinrich broke down how hitting top reliability means having lots of active feedback loops, and he even shared a handy diagram to show how it’s done.I Can OIDC You Clearly Now: How We Made Static Credentials a Thing of the PastThe team addressed the challenging issue of managing secrets in an open-source CI/CD pipeline by transitioning from static secrets to OIDC-based access, enhancing security and engineer empowerment. Rock around the Clock (Synchronization): Improve Performance with High Precision Time!Lerna Ekmekcioglu from Clockwork Systems discussed the crucial role of clock synchronization in addressing latency issues in distributed systems. She explained how it can be tough to pinpoint slowdowns, especially in complex environments like on-premises and cloud setups. The talk demonstrated how network contention impacts tail latencies and shared insights on various clock synchronization protocols, their pros and cons, and best practices for managing clock discipline. It was definitely one of the most interesting talks of the day!Managing CostThis session allowed everyone to come together and discuss cost management, facilitated by knowledgeable guides. It was an informal gathering rather than a prepared talk for questions and conversations among everyone interested in managing costs.Sailing the Database Seas: Applying SRE Principles at ScaleThe speaker shared valuable insights and real-world examples on topics like Monitoring Distributed Systems, Eliminating Toil, and Postmortem Culture. We walked away with practical ideas and guidelines to help us better understand and operate our database systems, including tips on selecting the right SLIs and SLOs.Selective Reliability Engineering: There Is No Single Source of TruthThe speakers took a look at some common confusion in system design and data modeling, while also thinking about bigger questions related to truth, the sources they trusted, and why those uncertainties really mattered.Panel Discussion: Is Reliability a Luxury Good?One of the highlights of the event was the panel discussion titled "Is Reliability a Luxury Good?" featuring insights from industry experts Andrew Ellam, Niall Murphy from Stanza, Joan O'Callaghan from Udemy, and Avleen Vig. Their diverse perspectives sparked thought-provoking discussions on the importance of building reliable systems and the trade-offs companies must consider when investing in reliability. Service Level ObjectivesThis session offered an open space for attendees to discuss SLOs with a few experts. It wasn’t a structured talk or workshop but a relaxed, interactive discussion where people could ask questions and connect with others interested in SLOs.Our team’s got some awesome merch with them, so don’t miss out—track us down and grab yours! 😎Last9 Booth at SRECon Dublin 2024I am already looking forward to Day 2 of SRECon Dublin 2024.Subscribe
If you’re an SRE—or know and love one—then you probably already know SRECon is the annual meetup for site reliability engineers.So, What’s SRECon All About?Hosted by USENIX, SRECon brings together everyone from newbies to industry legends, all eager to talk about what works, what fails spectacularly, and how we can keep pushing for more reliable, scalable tech. It’s a community-driven, solutions-oriented conference for anyone looking to up their reliability game.SRECon Dublin 2024New for 2024: The Discussion TrackThis year, SRECon introduced a fresh concept: the Discussion Track. It’s a space where attendees can go beyond presentations and have interactive discussions, led by experienced hosts who shape each session into whatever the group needs: an AMA, casual brainstorming, or an unconference vibe. Highlights from Day 1Here are some of the talks I enjoyed at SRECon Dublin 2024:Dude, You Forgot the Feedback: How Your Open Loop Control Planes Are Causing OutagesThe title alone brought people in. This session highlighted the risks of "fire and forget" control planes that lack real-time feedback, which can lead to outages. Laura walked through ways to design control planes that actively report on actions and their impacts, making systems more reliable and reducing operational errors.SRE Saga: The Song of Heroes and VillainsThis talk shared some great practical examples to help SRE teams build resilience and work better together when facing challenges. It also explored fun ways to tap into that "superhero" energy within the team, encouraging talent development while keeping everyone on the same page and accountable.The Frontiers of Reliability EngineeringThe discussion focused on three key frontiers they actively invested in: Data Operations and Monitoring Event-Based Systems, Mobile Observability, and Effective Management Practices for Reliability.Heinrich broke down how hitting top reliability means having lots of active feedback loops, and he even shared a handy diagram to show how it’s done.I Can OIDC You Clearly Now: How We Made Static Credentials a Thing of the PastThe team addressed the challenging issue of managing secrets in an open-source CI/CD pipeline by transitioning from static secrets to OIDC-based access, enhancing security and engineer empowerment. Rock around the Clock (Synchronization): Improve Performance with High Precision Time!Lerna Ekmekcioglu from Clockwork Systems discussed the crucial role of clock synchronization in addressing latency issues in distributed systems. She explained how it can be tough to pinpoint slowdowns, especially in complex environments like on-premises and cloud setups. The talk demonstrated how network contention impacts tail latencies and shared insights on various clock synchronization protocols, their pros and cons, and best practices for managing clock discipline. It was definitely one of the most interesting talks of the day!Managing CostThis session allowed everyone to come together and discuss cost management, facilitated by knowledgeable guides. It was an informal gathering rather than a prepared talk for questions and conversations among everyone interested in managing costs.Sailing the Database Seas: Applying SRE Principles at ScaleThe speaker shared valuable insights and real-world examples on topics like Monitoring Distributed Systems, Eliminating Toil, and Postmortem Culture. We walked away with practical ideas and guidelines to help us better understand and operate our database systems, including tips on selecting the right SLIs and SLOs.Selective Reliability Engineering: There Is No Single Source of TruthThe speakers took a look at some common confusion in system design and data modeling, while also thinking about bigger questions related to truth, the sources they trusted, and why those uncertainties really mattered.Panel Discussion: Is Reliability a Luxury Good?One of the highlights of the event was the panel discussion titled "Is Reliability a Luxury Good?" featuring insights from industry experts Andrew Ellam, Niall Murphy from Stanza, Joan O'Callaghan from Udemy, and Avleen Vig. Their diverse perspectives sparked thought-provoking discussions on the importance of building reliable systems and the trade-offs companies must consider when investing in reliability. Service Level ObjectivesThis session offered an open space for attendees to discuss SLOs with a few experts. It wasn’t a structured talk or workshop but a relaxed, interactive discussion where people could ask questions and connect with others interested in SLOs.Our team’s got some awesome merch with them, so don’t miss out—track us down and grab yours! 😎Last9 Booth at SRECon Dublin 2024I am already looking forward to Day 2 of SRECon Dublin 2024.Subscribe
Scaling Prometheus: Tips, Tricks, and Proven Strategies | Last9
Learn how to scale Prometheus with practical tips and strategies to keep your monitoring smooth and efficient, even as your needs grow!
 If you’re here, it’s safe to say your monitoring setup is facing some growing pains. Scaling Prometheus isn’t exactly plug-and-play—especially if your Kubernetes clusters or microservices are multiplying like bunnies. The more your infrastructure expands, the more you need a monitoring solution to keep up without buckling under the pressure.In this guide, we’ll talk about the whys and the hows of scaling Prometheus. We'll dig into the underlying concepts that make scaling Prometheus possible, plus the nuts-and-bolts strategies that make it work in the real world. Ready to level up your monitoring game?Understanding Prometheus ArchitectureBefore we jump into scaling Prometheus, let’s take a peek under the hood to see what makes it tick. Prometheus Core ComponentsCore ComponentsTime Series Database (TSDB)Data Storage: Prometheus’s TSDB isn’t your typical database—it’s designed specifically for handling time-series data. It stores metrics in a custom format optimized for quick access.Crash Recovery: It uses a Write-Ahead Log (WAL), which acts like a safety net, ensuring that your data stays intact even during unexpected crashes.Data Blocks: Instead of lumping all data together, TSDB organizes metrics in manageable, 2-hour blocks. This way, querying and processing data stay efficient, even as your data volume grows.ScraperMetric Collection: The scraper component is like Prometheus’s ears and eyes, continuously pulling metrics from predefined endpoints.Service Discovery: It handles automatic service discovery, so Prometheus always knows where to find new services without needing constant reconfiguration.Scrape Configurations: The scraper also lets you define scrape intervals and timeouts, tailoring how often data is collected based on your system’s needs.PromQL EngineQuery Processing: The PromQL engine is where all your queries get processed, making sense of the data stored in TSDB.Aggregations & Transformations: It’s built for powerful data transformations and aggregations, making it possible to slice and dice metrics in almost any way you need.Time-Based Operations: PromQL’s time-based capabilities let you compare metrics over different periods—a must-have for spotting trends or anomalies.💡If you're looking for setting up and configuring Alertmanager, we’ve got a handy guide that walks you through the process—check it out!The Pull Model ExplainedPrometheus uses a pull model, meaning it actively scrapes metrics from your endpoints rather than waiting for metrics to be pushed. This model is perfect for controlled, precise monitoring. Here’s an example configuration:scrape_configs: - job_name: 'node' static_configs: - targets: ['localhost:9100'] scrape_interval: 15s scrape_timeout: 10s metrics_path: /metrics scheme: httpBenefits of the Pull Model:Control Over Failure Detection: Prometheus can detect if a target fails to respond, giving you insight into the health of your endpoints.Firewall Friendliness: It’s generally easier to allow one-way traffic for scrapes than to configure permissions for every component.Simple Testing: You can verify endpoint availability and scrape configurations without a lot of troubleshooting.Scaling Strategies:When Prometheus starts to feel the weight of growing data and queries, it’s time to explore scaling. Here are three foundational strategies:1. Vertical ScalingThe simplest approach is to beef up your existing Prometheus instance with more memory, CPU, and storage. Here’s a sample configuration for optimizing Prometheus’s performance:global: scrape_interval: 15s evaluation_interval: 15s storage: tsdb: retention: time: 15d size: 512GB wal-compression: true exemplars: max-exemplars: 100000 query: max-samples: 50000000 timeout: 2mKey Considerations:Monitor TSDB Compaction: Regularly check TSDB compaction metrics, as they’re essential for data storage efficiency.Watch WAL Performance: Keep an eye on WAL metrics to ensure smooth crash recovery.Track Memory Usage: As data volume grows, memory demands will too—tracking this helps avoid resource issues.📝Check out our guide on Prometheus RemoteWrite Exporter to get all the details you need!2. Horizontal Scaling Through FederationFederation allows you to create a multi-tiered Prometheus setup, which is a great way to scale while keeping monitoring organized. Here’s a basic configuration:# Global Prometheus configurationscrape_configs: - job_name: 'federate' scrape_interval: 15s honor_labels: true metrics_path: '/federate' params: 'match[]': - '{job="node"}' - '{job="kubernetes-pods"}' - '{__name__=~"job:.*"}' static_configs: - targets: - 'prometheus-app:9090' - 'prometheus-infra:9090' # Recording rules for federationrules: - record: job:node_memory_utilization:avg expr: avg(node_memory_used_bytes / node_memory_total_bytes)Advanced Scaling SolutionsWhen Prometheus alone isn’t enough, tools like Thanos and Cortex can extend their capabilities for long-term storage and high-demand environments.Thanos Architecture and ImplementationThanos adds long-term storage and global querying. Here’s a basic setup:apiVersion: apps/v1kind: Deploymentmetadata: name: thanos-queryspec: replicas: 3 template: spec: containers: - name: thanos-query image: quay.io/thanos/thanos:v0.24.0 args: - 'query' - '--store=dnssrv+_grpc._tcp.thanos-store' - '--store=dnssrv+_grpc._tcp.thanos-sidecar'Cortex for Cloud-Native DeploymentsIf you’re in a cloud-native environment, Cortex offers the following benefits:Dynamic Scaling: It can scale with your infrastructure automatically.Multi-Tenant Isolation: The Cortex is built for multi-tenancy, keeping each environment isolated.Cloud Storage Integration: Cortex connects seamlessly with cloud storage for long-term retention.Query Caching: It offers query caching to improve performance under heavy load.📖Check out our guide on Prometheus Recording Rules—it's a great resource if you're working with Prometheus and looking to optimize your setup!Practical Performance OptimizationTo keep Prometheus running smoothly, here are some optimization tips:1. Query OptimizationAvoid complex or redundant PromQL queries that could slow down Prometheus. For example:Before:rate(http_requests_total[5m]) or rate(http_requests_total[5m] offset 5m)After:rate(http_requests_total[5m])2. Recording RulesFor frequently-used, heavy queries, recording rules can lighten the load:groups: - name: example rules: - record: job:http_inprogress_requests:sum expr: sum(http_inprogress_requests) by (job)3. Label ManagementAvoid high-cardinality labels, as they can create performance issues.Good Label Usage:metric_name{service="payment", endpoint="/api/v1/pay"}Probo Cuts Monitoring Costs by 90% with Last9 | Last9Read how Probo uses Last9 as an alternative to New Relic and Cloudwatch for infrastructure monitoring.Download PDFMonitoring Your Prometheus InstanceKeeping Prometheus itself healthy requires monitoring key metrics:TSDB Metrics:rate(prometheus_tsdb_head_samples_appended_total[5m]) prometheus_tsdb_head_seriesScrape Performance:To monitor the performance of your scrape targets, use the following query to track the rate of scrapes that exceeded the sample limit:rate(prometheus_target_scrapes_exceeded_sample_limit_total[5m]) prometheus_target_scrape_pool_targetsQuery Performance:To evaluate the performance of your queries, this query measures the rate of query execution duration:rate(prometheus_engine_query_duration_seconds_count[5m])Troubleshooting GuideScaling can introduce new challenges, so here are some common issues and quick solutions to keep Prometheus running smoothly:High Memory UsageHigh memory consumption often points to high-cardinality metrics or inefficient queries. Here are some steps to diagnose and mitigate:# Check series cardinalitycurl -G http://localhost:9090/api/v1/status/tsdb # Monitor memory usage in real-timecontainer_memory_usage_bytes{container="prometheus"}Tip: Keep an eye on your metrics’ labels and reduce unnecessary ones. High-cardinality labels can quickly inflate memory use.Slow QueriesIf queries are slowing down, it’s time to check what’s running under the hood:# Enable query logging for insights into problematic queries--query.log-queries=true # Monitor query performance to spot bottlenecksrate(prometheus_engine_query_duration_seconds_sum[5m])Tip: Implement recording rules to pre-compute frequently accessed metrics, reducing load on Prometheus when running complex queries.ConclusionScaling Prometheus isn’t just about adding more power—it’s about understanding when and how to grow to fit your needs. With the right strategies, you’ll keep Prometheus performing well, no matter how your infrastructure grows.🤝If you’re keen to chat or have any questions, feel free to join our Discord community! We have a dedicated channel where you can connect with other developers and discuss your specific use cases.FAQsCan you scale Prometheus?Yes! Prometheus can be scaled both vertically (by increasing resources on a single instance) and horizontally (through federation or by using solutions like Thanos or Cortex for distributed setups).How well does Prometheus scale?Prometheus scales effectively for most use cases, especially when combined with federation for hierarchical setups or long-term storage solutions like Thanos. However, it’s ideal for monitoring individual services and clusters rather than being a one-size-fits-all centralized solution.What is Federated Prometheus?Federated Prometheus refers to a setup where multiple Prometheus servers work in a hierarchical structure. Each “child” instance gathers data from a specific part of your infrastructure, and a “parent” Prometheus instance collects summaries, making it easier to manage large, distributed environments.Is Prometheus pull or push?Prometheus operates on a pull-based model, meaning it scrapes (pulls) metrics from endpoints at regular intervals, rather than having metrics pushed to it.How can you orchestrate Prometheus?You can orchestrate Prometheus on Kubernetes using custom resources like Prometheus Operator, which simplifies the deployment, configuration, and management of Prometheus and related services.What is the default Prometheus configuration?In its default configuration, Prometheus has a retention period of 15 days for time-series data, uses local storage, and scrapes metrics every 1 minute. However, these settings can be customized based on your needs.What is the difference between Prometheus and Graphite?Prometheus and Graphite both handle time-series data but have different design philosophies. Prometheus uses a pull model, has its query language (PromQL), and supports alerting natively, while Graphite uses a push model and relies on external tools for alerting and query functionalities.How does Prometheus compare to Ganglia?Prometheus is more modern and flexible than Ganglia, especially in dynamic, containerized environments. Prometheus offers better support for cloud-native systems, more powerful query capabilities, and better integration with Kubernetes.What is the best way to integrate Prometheus with your organization's existing monitoring system?Integrate Prometheus with existing systems using exporters, AlertManager for notifications, and tools like Grafana for visualizations. Additionally, consider using Federation or Thanos to bridge Prometheus data with other systems.What are the benefits of Federated Prometheus?Federated Prometheus offers scalable monitoring for large, distributed environments. It enables targeted scraping across multiple Prometheus instances, reduces data redundancy, and optimizes resource usage by dividing and conquering.SubscribeDownload PDF
If you’re here, it’s safe to say your monitoring setup is facing some growing pains. Scaling Prometheus isn’t exactly plug-and-play—especially if your Kubernetes clusters or microservices are multiplying like bunnies. The more your infrastructure expands, the more you need a monitoring solution to keep up without buckling under the pressure.In this guide, we’ll talk about the whys and the hows of scaling Prometheus. We'll dig into the underlying concepts that make scaling Prometheus possible, plus the nuts-and-bolts strategies that make it work in the real world. Ready to level up your monitoring game?Understanding Prometheus ArchitectureBefore we jump into scaling Prometheus, let’s take a peek under the hood to see what makes it tick. Prometheus Core ComponentsCore ComponentsTime Series Database (TSDB)Data Storage: Prometheus’s TSDB isn’t your typical database—it’s designed specifically for handling time-series data. It stores metrics in a custom format optimized for quick access.Crash Recovery: It uses a Write-Ahead Log (WAL), which acts like a safety net, ensuring that your data stays intact even during unexpected crashes.Data Blocks: Instead of lumping all data together, TSDB organizes metrics in manageable, 2-hour blocks. This way, querying and processing data stay efficient, even as your data volume grows.ScraperMetric Collection: The scraper component is like Prometheus’s ears and eyes, continuously pulling metrics from predefined endpoints.Service Discovery: It handles automatic service discovery, so Prometheus always knows where to find new services without needing constant reconfiguration.Scrape Configurations: The scraper also lets you define scrape intervals and timeouts, tailoring how often data is collected based on your system’s needs.PromQL EngineQuery Processing: The PromQL engine is where all your queries get processed, making sense of the data stored in TSDB.Aggregations & Transformations: It’s built for powerful data transformations and aggregations, making it possible to slice and dice metrics in almost any way you need.Time-Based Operations: PromQL’s time-based capabilities let you compare metrics over different periods—a must-have for spotting trends or anomalies.💡If you're looking for setting up and configuring Alertmanager, we’ve got a handy guide that walks you through the process—check it out!The Pull Model ExplainedPrometheus uses a pull model, meaning it actively scrapes metrics from your endpoints rather than waiting for metrics to be pushed. This model is perfect for controlled, precise monitoring. Here’s an example configuration:scrape_configs: - job_name: 'node' static_configs: - targets: ['localhost:9100'] scrape_interval: 15s scrape_timeout: 10s metrics_path: /metrics scheme: httpBenefits of the Pull Model:Control Over Failure Detection: Prometheus can detect if a target fails to respond, giving you insight into the health of your endpoints.Firewall Friendliness: It’s generally easier to allow one-way traffic for scrapes than to configure permissions for every component.Simple Testing: You can verify endpoint availability and scrape configurations without a lot of troubleshooting.Scaling Strategies:When Prometheus starts to feel the weight of growing data and queries, it’s time to explore scaling. Here are three foundational strategies:1. Vertical ScalingThe simplest approach is to beef up your existing Prometheus instance with more memory, CPU, and storage. Here’s a sample configuration for optimizing Prometheus’s performance:global: scrape_interval: 15s evaluation_interval: 15s storage: tsdb: retention: time: 15d size: 512GB wal-compression: true exemplars: max-exemplars: 100000 query: max-samples: 50000000 timeout: 2mKey Considerations:Monitor TSDB Compaction: Regularly check TSDB compaction metrics, as they’re essential for data storage efficiency.Watch WAL Performance: Keep an eye on WAL metrics to ensure smooth crash recovery.Track Memory Usage: As data volume grows, memory demands will too—tracking this helps avoid resource issues.📝Check out our guide on Prometheus RemoteWrite Exporter to get all the details you need!2. Horizontal Scaling Through FederationFederation allows you to create a multi-tiered Prometheus setup, which is a great way to scale while keeping monitoring organized. Here’s a basic configuration:# Global Prometheus configurationscrape_configs: - job_name: 'federate' scrape_interval: 15s honor_labels: true metrics_path: '/federate' params: 'match[]': - '{job="node"}' - '{job="kubernetes-pods"}' - '{__name__=~"job:.*"}' static_configs: - targets: - 'prometheus-app:9090' - 'prometheus-infra:9090' # Recording rules for federationrules: - record: job:node_memory_utilization:avg expr: avg(node_memory_used_bytes / node_memory_total_bytes)Advanced Scaling SolutionsWhen Prometheus alone isn’t enough, tools like Thanos and Cortex can extend their capabilities for long-term storage and high-demand environments.Thanos Architecture and ImplementationThanos adds long-term storage and global querying. Here’s a basic setup:apiVersion: apps/v1kind: Deploymentmetadata: name: thanos-queryspec: replicas: 3 template: spec: containers: - name: thanos-query image: quay.io/thanos/thanos:v0.24.0 args: - 'query' - '--store=dnssrv+_grpc._tcp.thanos-store' - '--store=dnssrv+_grpc._tcp.thanos-sidecar'Cortex for Cloud-Native DeploymentsIf you’re in a cloud-native environment, Cortex offers the following benefits:Dynamic Scaling: It can scale with your infrastructure automatically.Multi-Tenant Isolation: The Cortex is built for multi-tenancy, keeping each environment isolated.Cloud Storage Integration: Cortex connects seamlessly with cloud storage for long-term retention.Query Caching: It offers query caching to improve performance under heavy load.📖Check out our guide on Prometheus Recording Rules—it's a great resource if you're working with Prometheus and looking to optimize your setup!Practical Performance OptimizationTo keep Prometheus running smoothly, here are some optimization tips:1. Query OptimizationAvoid complex or redundant PromQL queries that could slow down Prometheus. For example:Before:rate(http_requests_total[5m]) or rate(http_requests_total[5m] offset 5m)After:rate(http_requests_total[5m])2. Recording RulesFor frequently-used, heavy queries, recording rules can lighten the load:groups: - name: example rules: - record: job:http_inprogress_requests:sum expr: sum(http_inprogress_requests) by (job)3. Label ManagementAvoid high-cardinality labels, as they can create performance issues.Good Label Usage:metric_name{service="payment", endpoint="/api/v1/pay"}Probo Cuts Monitoring Costs by 90% with Last9 | Last9Read how Probo uses Last9 as an alternative to New Relic and Cloudwatch for infrastructure monitoring.Download PDFMonitoring Your Prometheus InstanceKeeping Prometheus itself healthy requires monitoring key metrics:TSDB Metrics:rate(prometheus_tsdb_head_samples_appended_total[5m]) prometheus_tsdb_head_seriesScrape Performance:To monitor the performance of your scrape targets, use the following query to track the rate of scrapes that exceeded the sample limit:rate(prometheus_target_scrapes_exceeded_sample_limit_total[5m]) prometheus_target_scrape_pool_targetsQuery Performance:To evaluate the performance of your queries, this query measures the rate of query execution duration:rate(prometheus_engine_query_duration_seconds_count[5m])Troubleshooting GuideScaling can introduce new challenges, so here are some common issues and quick solutions to keep Prometheus running smoothly:High Memory UsageHigh memory consumption often points to high-cardinality metrics or inefficient queries. Here are some steps to diagnose and mitigate:# Check series cardinalitycurl -G http://localhost:9090/api/v1/status/tsdb # Monitor memory usage in real-timecontainer_memory_usage_bytes{container="prometheus"}Tip: Keep an eye on your metrics’ labels and reduce unnecessary ones. High-cardinality labels can quickly inflate memory use.Slow QueriesIf queries are slowing down, it’s time to check what’s running under the hood:# Enable query logging for insights into problematic queries--query.log-queries=true # Monitor query performance to spot bottlenecksrate(prometheus_engine_query_duration_seconds_sum[5m])Tip: Implement recording rules to pre-compute frequently accessed metrics, reducing load on Prometheus when running complex queries.ConclusionScaling Prometheus isn’t just about adding more power—it’s about understanding when and how to grow to fit your needs. With the right strategies, you’ll keep Prometheus performing well, no matter how your infrastructure grows.🤝If you’re keen to chat or have any questions, feel free to join our Discord community! We have a dedicated channel where you can connect with other developers and discuss your specific use cases.FAQsCan you scale Prometheus?Yes! Prometheus can be scaled both vertically (by increasing resources on a single instance) and horizontally (through federation or by using solutions like Thanos or Cortex for distributed setups).How well does Prometheus scale?Prometheus scales effectively for most use cases, especially when combined with federation for hierarchical setups or long-term storage solutions like Thanos. However, it’s ideal for monitoring individual services and clusters rather than being a one-size-fits-all centralized solution.What is Federated Prometheus?Federated Prometheus refers to a setup where multiple Prometheus servers work in a hierarchical structure. Each “child” instance gathers data from a specific part of your infrastructure, and a “parent” Prometheus instance collects summaries, making it easier to manage large, distributed environments.Is Prometheus pull or push?Prometheus operates on a pull-based model, meaning it scrapes (pulls) metrics from endpoints at regular intervals, rather than having metrics pushed to it.How can you orchestrate Prometheus?You can orchestrate Prometheus on Kubernetes using custom resources like Prometheus Operator, which simplifies the deployment, configuration, and management of Prometheus and related services.What is the default Prometheus configuration?In its default configuration, Prometheus has a retention period of 15 days for time-series data, uses local storage, and scrapes metrics every 1 minute. However, these settings can be customized based on your needs.What is the difference between Prometheus and Graphite?Prometheus and Graphite both handle time-series data but have different design philosophies. Prometheus uses a pull model, has its query language (PromQL), and supports alerting natively, while Graphite uses a push model and relies on external tools for alerting and query functionalities.How does Prometheus compare to Ganglia?Prometheus is more modern and flexible than Ganglia, especially in dynamic, containerized environments. Prometheus offers better support for cloud-native systems, more powerful query capabilities, and better integration with Kubernetes.What is the best way to integrate Prometheus with your organization's existing monitoring system?Integrate Prometheus with existing systems using exporters, AlertManager for notifications, and tools like Grafana for visualizations. Additionally, consider using Federation or Thanos to bridge Prometheus data with other systems.What are the benefits of Federated Prometheus?Federated Prometheus offers scalable monitoring for large, distributed environments. It enables targeted scraping across multiple Prometheus instances, reduces data redundancy, and optimizes resource usage by dividing and conquering.SubscribeDownload PDF
Getting Started with Host Metrics Using OpenTelemetry | Last9
Learn to monitor host metrics with OpenTelemetry. Discover setup tips, common pitfalls, and best practices for effective observability.
 After years of working with monitoring solutions at both startups and big-name companies, I've realized something important: knowing why you’re doing something is just as crucial as knowing how to do it. When we talk about host metrics monitoring, it’s not just about gathering data; it’s about figuring out what that data means and why it’s important for you.In this guide, I want to help you make sense of host metrics monitoring with OpenTelemetry Collector. We'll explore how these metrics can give you valuable insights into your systems and help you keep everything running smoothly.What are Host Metrics?Host metrics represent essential performance indicators of a server’s operation. These metrics help monitor resource utilization and system behavior, allowing for effective infrastructure management.Key host metrics include:CPU Utilization: The percentage of CPU capacity being used.Memory Usage: The amount of RAM consumed by the system.Filesystem: Disk space availability and I/O operations.Network Interface: Data transfer rates and network connectivity.Process CPU: CPU usage of individual system processes.These metrics provide critical insights into the performance and operational status of a host.What are OpenTelemetry Metrics? A Comprehensive Guide | Last9Learn about OpenTelemetry Metrics, types of instruments, and best practices for effective application performance monitoring and observability.Last9Book a DemoThe OpenTelemetry Collector ArchitectureThe OpenTelemetry Collector operates on a pipeline architecture, designed to collect, process, and export telemetry data efficiently.Key ComponentsReceivers: These are the entry points for data collection, responsible for gathering metrics, logs, and traces from various sources. For host metrics, we use the host metrics receiver.Processors: These components handle data transformation, enrichment, or aggregation. They can apply modifications such as batching, filtering, or adding metadata before forwarding the data to the exporters.Exporters: These send the processed telemetry data to a destination, such as Prometheus, OTLP (OpenTelemetry Protocol), or other monitoring and observability platforms.The data flow through the pipeline looks like this:Otel Collector ArchitectureImplementing OpenTelemetry in Your Environment1. Basic Setup (Development Environment)To start with a simple local setup, here’s a minimal configuration that I use for development. It includes the hostmetrics receiver for collecting basic metrics like CPU and memory usage, with the data exported to Prometheus.# config.yaml - Development Setupreceivers: hostmetrics: collection_interval: 30s scrapers: cpu: {} memory: {}processors: resource: attributes: - action: insert key: service.name value: "host-monitor-dev" - action: insert key: env value: "development"exporters: prometheus: endpoint: "0.0.0.0:8889"service: pipelines: metrics: receivers: [hostmetrics] processors: [resource] exporters: [prometheus]Start the OpenTelemetry Collector with debug logging to ensure everything works correctly:# Start the collector with debug loggingotelcol-contrib --config config.yaml --set=service.telemetry.logs.level=debugOpenTelemetry Collector: The Complete Guide | Last9This guide covers the OpenTelemetry Collector, its features, use cases, and tips for effectively managing telemetry data.Last92. Production ConfigurationFor production, a more robust setup is recommended, incorporating multiple exporters and enhanced metadata for better observability. This example adds more detailed metrics and uses environment-specific variables.# config.yaml - Production Setupreceivers: hostmetrics: collection_interval: 10s scrapers: cpu: metrics: system.cpu.utilization: enabled: true memory: metrics: system.memory.utilization: enabled: true disk: {} filesystem: {} network: metrics: system.network.io: enabled: trueprocessors: resource: attributes: - action: insert key: service.name value: ${SERVICE_NAME} - action: insert key: environment value: ${ENV} resourcedetection: detectors: [env, system, gcp, azure] timeout: 2sexporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: ${OTLP_INSECURE} prometheus: endpoint: "localhost:8889"service: pipelines: metrics: receivers: [hostmetrics] processors: [resource, resourcedetection] exporters: [otlp, prometheus]This production configuration ensures low-latency metric collection and supports exporting to both Prometheus and an OTLP-compatible endpoint, useful for integrating with larger observability platforms.3. Kubernetes DeploymentFor Kubernetes environments, deploying the OpenTelemetry Collector as a DaemonSet ensures that metrics are gathered from every node in the cluster. Below is a configuration for deploying the collector on Kubernetes.ConfigMap for Collector ConfigurationThe ConfigMap contains the collector configuration, defining how the metrics are scraped and where they are exported.# kubernetes/collector-config.yamlapiVersion: v1kind: ConfigMapmetadata: name: otel-collector-configdata: config.yaml: | receivers: hostmetrics: collection_interval: 30s scrapers: cpu: {} memory: {} disk: {} filesystem: {} network: {} process: {} processors: resource: attributes: - action: insert key: cluster.name value: ${CLUSTER_NAME} resourcedetection: detectors: [kubernetes] timeout: 5s exporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: false cert_file: /etc/certs/collector.crt key_file: /etc/certs/collector.key service: pipelines: metrics: receivers: [hostmetrics] processors: [resource, resourcedetection] exporters: [otlp]This ConfigMap defines the receivers, processors, and exporters necessary for collecting host metrics from the nodes and sending them to an OTLP endpoint. The resource processor adds metadata about the cluster, while the resourcedetection processor uses the Kubernetes detector to gather node-specific metadata.OpenTelemetry Protocol (OTLP): A Deep Dive into Observability | Last9Learn about OTLP’s key features, and how it simplifies telemetry data handling, and get practical tips for implementation.Last9DaemonSet for Collector DeploymentThe DaemonSet ensures that one instance of the collector runs on every node in the cluster.# kubernetes/daemonset.yamlapiVersion: apps/v1kind: DaemonSetmetadata: name: otel-collectorspec: selector: matchLabels: app: otel-collector template: metadata: labels: app: otel-collector spec: containers: - name: otel-collector image: otel/opentelemetry-collector-contrib:latest resources: limits: cpu: 200m memory: 200Mi requests: cpu: 100m memory: 100Mi volumeMounts: - name: config mountPath: /etc/otelcol/config.yaml subPath: config.yaml env: - name: CLUSTER_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: OTLP_ENDPOINT value: "your-otlp-endpoint" volumes: - name: config configMap: name: otel-collector-configIn this DaemonSet configuration:The otel-collector container is deployed on every node.The CLUSTER_NAME environment variable is injected dynamically based on the node’s metadata.Metrics are exported to the specified OTLP endpoint, making it compatible with cloud-based or self-hosted observability backends.This setup ensures an efficient collection of host metrics from all nodes in a Kubernetes cluster, making it ideal for large-scale environments.Common Pitfalls and SolutionsWhen implementing the OpenTelemetry Collector in a production environment, there are several common challenges you might encounter. Here’s a look at these pitfalls along with solutions to address them.1. High CPU Usage in ProductionIssue: If you notice high CPU utilization from the collector itself, it may be due to a short collection interval that generates excessive load.Solution: Adjust the collection interval to reduce the frequency of data collection, allowing the collector to operate more efficiently.receivers: hostmetrics: collection_interval: 60s # Increase from default 30s2. Missing Permissions on LinuxIssue: When running the OpenTelemetry Collector without root privileges, you might encounter permission errors, particularly when trying to access disk metrics.Solution: Grant the necessary capabilities to the collector binary to allow it to access the required system resources.# Add capabilities for disk metricssudo setcap cap_dac_read_search=+ep /usr/local/bin/otelcol-contribHow to Use Jaeger with OpenTelemetry | Last9This guide shows you how to easily use Jaeger with OpenTelemetry for improved tracing and application monitoring.Last93. Memory Leaks in Long-Running InstancesIssue: In some cases, long-running instances of the collector can exhibit memory leaks, especially if too many processors are configured.Solution: Optimize the processor chain to include memory-limiting configurations to prevent excessive memory usage.processors: batch: timeout: 10s send_batch_size: 1024 memory_limiter: check_interval: 5s limit_mib: 150Best Practices from ProductionWhen deploying the OpenTelemetry Collector, adhering to best practices can significantly improve the efficiency and reliability of your monitoring setup. Here are some recommendations based on production experience:1. Resource AttributionAlways use the resource detection processor to automatically identify and enrich telemetry data with cloud metadata. This enhances the context of the metrics collected, making it easier to understand the performance and health of your applications within the infrastructure.processors: resourcedetection: detectors: [env, system, gcp, azure] timeout: 2s2. Monitoring the MonitorSet up alerting mechanisms on the collector's own metrics. By monitoring the health and performance of the collector itself, you can quickly identify issues before they affect your overall observability stack.3. Graceful DegradationConfigure timeout and retry policies for exporters to ensure that transient issues don’t lead to data loss. Implementing these policies allows the system to handle temporary failures gracefully without impacting the overall monitoring setup.exporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: ${OTLP_INSECURE} timeout: 10s retry_on_failure: enabled: true attempts: 3 interval: 5s4. Versioning and UpgradesRegularly update the OpenTelemetry Collector to leverage the latest features, improvements, and bug fixes. Always test new versions in a staging environment before rolling them out to production to ensure compatibility with your existing setup.5. Configuration ManagementMaintain a version-controlled repository for your configuration files. This allows for easier tracking of changes, rollbacks when necessary, and collaboration across teams.Reliable Observability for 25+ million concurrent live-streaming viewers | Last9How we’ve tackled high cardinality metrics with long-term retention for one of the largest video streaming companies.Download PDFConclusionGetting a handle on host metrics monitoring with OpenTelemetry is like having a roadmap for your system’s performance. With the right setup, you’ll not only collect valuable data but also gain insights that can help you make smarter decisions about your infrastructure.🤝If you’re still eager to chat or have questions, our community on Discord is open. We’ve got a dedicated channel where you can have discussions with other developers about your specific use case.FAQsWhat does an OpenTelemetry Collector do?The OpenTelemetry Collector is like a central hub for telemetry data. It receives, processes, and exports logs, metrics, and traces from various sources, making it easier to monitor and analyze your systems without being tied to a specific vendor.What are host metrics?Host metrics are performance indicators that give you a glimpse into how your server is doing. They include things like CPU utilization, memory usage, disk space availability, network throughput, and the CPU usage of individual processes. These metrics are essential for keeping an eye on resource utilization and ensuring your infrastructure runs smoothly.What is the difference between telemetry and OpenTelemetry?Telemetry is the general term for collecting and sending data from remote sources to a system for monitoring and analysis. OpenTelemetry, on the other hand, is a specific framework with APIs designed for generating, collecting, and exporting telemetry data—logs, metrics, and traces—in a standardized way. It provides developers with the tools to instrument their applications effectively.Is the OpenTelemetry Collector observable?Absolutely! The OpenTelemetry Collector is observable itself. It generates its own telemetry data, such as metrics and logs, that you can monitor to evaluate its performance and health. This includes tracking things like resource usage, processing latency, and error rates, ensuring it operates effectively.What is the difference between OpenTelemetry Collector and Prometheus?While both are important in observability, they play different roles. The OpenTelemetry Collector acts as a data pipeline, collecting, processing, and exporting telemetry data. Prometheus is a monitoring and alerting toolkit specifically designed for storing and querying time-series data. You can scrape metrics from the OpenTelemetry Collector using Prometheus, and the collector can also export metrics directly to Prometheus.How do you configure the OpenTelemetry Collector to monitor host metrics?To configure the OpenTelemetry Collector for host metrics monitoring, set up a hostmetrics receiver in the configuration file. Specify the collection interval and the types of metrics you want to collect (like CPU, memory, disk, and network). Then, configure processors and exporters to handle and send the collected data to your chosen monitoring platform.How do you set up HostMetrics monitoring with the OpenTelemetry Collector?Setting up HostMetrics monitoring is straightforward. Create a configuration file that includes the HostMetrics receiver, define the metrics you want to collect, and specify an exporter to send the data to your monitoring solution (like Prometheus). Once your configuration is ready, start the collector with the file you created.Subscribe
After years of working with monitoring solutions at both startups and big-name companies, I've realized something important: knowing why you’re doing something is just as crucial as knowing how to do it. When we talk about host metrics monitoring, it’s not just about gathering data; it’s about figuring out what that data means and why it’s important for you.In this guide, I want to help you make sense of host metrics monitoring with OpenTelemetry Collector. We'll explore how these metrics can give you valuable insights into your systems and help you keep everything running smoothly.What are Host Metrics?Host metrics represent essential performance indicators of a server’s operation. These metrics help monitor resource utilization and system behavior, allowing for effective infrastructure management.Key host metrics include:CPU Utilization: The percentage of CPU capacity being used.Memory Usage: The amount of RAM consumed by the system.Filesystem: Disk space availability and I/O operations.Network Interface: Data transfer rates and network connectivity.Process CPU: CPU usage of individual system processes.These metrics provide critical insights into the performance and operational status of a host.What are OpenTelemetry Metrics? A Comprehensive Guide | Last9Learn about OpenTelemetry Metrics, types of instruments, and best practices for effective application performance monitoring and observability.Last9Book a DemoThe OpenTelemetry Collector ArchitectureThe OpenTelemetry Collector operates on a pipeline architecture, designed to collect, process, and export telemetry data efficiently.Key ComponentsReceivers: These are the entry points for data collection, responsible for gathering metrics, logs, and traces from various sources. For host metrics, we use the host metrics receiver.Processors: These components handle data transformation, enrichment, or aggregation. They can apply modifications such as batching, filtering, or adding metadata before forwarding the data to the exporters.Exporters: These send the processed telemetry data to a destination, such as Prometheus, OTLP (OpenTelemetry Protocol), or other monitoring and observability platforms.The data flow through the pipeline looks like this:Otel Collector ArchitectureImplementing OpenTelemetry in Your Environment1. Basic Setup (Development Environment)To start with a simple local setup, here’s a minimal configuration that I use for development. It includes the hostmetrics receiver for collecting basic metrics like CPU and memory usage, with the data exported to Prometheus.# config.yaml - Development Setupreceivers: hostmetrics: collection_interval: 30s scrapers: cpu: {} memory: {}processors: resource: attributes: - action: insert key: service.name value: "host-monitor-dev" - action: insert key: env value: "development"exporters: prometheus: endpoint: "0.0.0.0:8889"service: pipelines: metrics: receivers: [hostmetrics] processors: [resource] exporters: [prometheus]Start the OpenTelemetry Collector with debug logging to ensure everything works correctly:# Start the collector with debug loggingotelcol-contrib --config config.yaml --set=service.telemetry.logs.level=debugOpenTelemetry Collector: The Complete Guide | Last9This guide covers the OpenTelemetry Collector, its features, use cases, and tips for effectively managing telemetry data.Last92. Production ConfigurationFor production, a more robust setup is recommended, incorporating multiple exporters and enhanced metadata for better observability. This example adds more detailed metrics and uses environment-specific variables.# config.yaml - Production Setupreceivers: hostmetrics: collection_interval: 10s scrapers: cpu: metrics: system.cpu.utilization: enabled: true memory: metrics: system.memory.utilization: enabled: true disk: {} filesystem: {} network: metrics: system.network.io: enabled: trueprocessors: resource: attributes: - action: insert key: service.name value: ${SERVICE_NAME} - action: insert key: environment value: ${ENV} resourcedetection: detectors: [env, system, gcp, azure] timeout: 2sexporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: ${OTLP_INSECURE} prometheus: endpoint: "localhost:8889"service: pipelines: metrics: receivers: [hostmetrics] processors: [resource, resourcedetection] exporters: [otlp, prometheus]This production configuration ensures low-latency metric collection and supports exporting to both Prometheus and an OTLP-compatible endpoint, useful for integrating with larger observability platforms.3. Kubernetes DeploymentFor Kubernetes environments, deploying the OpenTelemetry Collector as a DaemonSet ensures that metrics are gathered from every node in the cluster. Below is a configuration for deploying the collector on Kubernetes.ConfigMap for Collector ConfigurationThe ConfigMap contains the collector configuration, defining how the metrics are scraped and where they are exported.# kubernetes/collector-config.yamlapiVersion: v1kind: ConfigMapmetadata: name: otel-collector-configdata: config.yaml: | receivers: hostmetrics: collection_interval: 30s scrapers: cpu: {} memory: {} disk: {} filesystem: {} network: {} process: {} processors: resource: attributes: - action: insert key: cluster.name value: ${CLUSTER_NAME} resourcedetection: detectors: [kubernetes] timeout: 5s exporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: false cert_file: /etc/certs/collector.crt key_file: /etc/certs/collector.key service: pipelines: metrics: receivers: [hostmetrics] processors: [resource, resourcedetection] exporters: [otlp]This ConfigMap defines the receivers, processors, and exporters necessary for collecting host metrics from the nodes and sending them to an OTLP endpoint. The resource processor adds metadata about the cluster, while the resourcedetection processor uses the Kubernetes detector to gather node-specific metadata.OpenTelemetry Protocol (OTLP): A Deep Dive into Observability | Last9Learn about OTLP’s key features, and how it simplifies telemetry data handling, and get practical tips for implementation.Last9DaemonSet for Collector DeploymentThe DaemonSet ensures that one instance of the collector runs on every node in the cluster.# kubernetes/daemonset.yamlapiVersion: apps/v1kind: DaemonSetmetadata: name: otel-collectorspec: selector: matchLabels: app: otel-collector template: metadata: labels: app: otel-collector spec: containers: - name: otel-collector image: otel/opentelemetry-collector-contrib:latest resources: limits: cpu: 200m memory: 200Mi requests: cpu: 100m memory: 100Mi volumeMounts: - name: config mountPath: /etc/otelcol/config.yaml subPath: config.yaml env: - name: CLUSTER_NAME valueFrom: fieldRef: fieldPath: metadata.name - name: OTLP_ENDPOINT value: "your-otlp-endpoint" volumes: - name: config configMap: name: otel-collector-configIn this DaemonSet configuration:The otel-collector container is deployed on every node.The CLUSTER_NAME environment variable is injected dynamically based on the node’s metadata.Metrics are exported to the specified OTLP endpoint, making it compatible with cloud-based or self-hosted observability backends.This setup ensures an efficient collection of host metrics from all nodes in a Kubernetes cluster, making it ideal for large-scale environments.Common Pitfalls and SolutionsWhen implementing the OpenTelemetry Collector in a production environment, there are several common challenges you might encounter. Here’s a look at these pitfalls along with solutions to address them.1. High CPU Usage in ProductionIssue: If you notice high CPU utilization from the collector itself, it may be due to a short collection interval that generates excessive load.Solution: Adjust the collection interval to reduce the frequency of data collection, allowing the collector to operate more efficiently.receivers: hostmetrics: collection_interval: 60s # Increase from default 30s2. Missing Permissions on LinuxIssue: When running the OpenTelemetry Collector without root privileges, you might encounter permission errors, particularly when trying to access disk metrics.Solution: Grant the necessary capabilities to the collector binary to allow it to access the required system resources.# Add capabilities for disk metricssudo setcap cap_dac_read_search=+ep /usr/local/bin/otelcol-contribHow to Use Jaeger with OpenTelemetry | Last9This guide shows you how to easily use Jaeger with OpenTelemetry for improved tracing and application monitoring.Last93. Memory Leaks in Long-Running InstancesIssue: In some cases, long-running instances of the collector can exhibit memory leaks, especially if too many processors are configured.Solution: Optimize the processor chain to include memory-limiting configurations to prevent excessive memory usage.processors: batch: timeout: 10s send_batch_size: 1024 memory_limiter: check_interval: 5s limit_mib: 150Best Practices from ProductionWhen deploying the OpenTelemetry Collector, adhering to best practices can significantly improve the efficiency and reliability of your monitoring setup. Here are some recommendations based on production experience:1. Resource AttributionAlways use the resource detection processor to automatically identify and enrich telemetry data with cloud metadata. This enhances the context of the metrics collected, making it easier to understand the performance and health of your applications within the infrastructure.processors: resourcedetection: detectors: [env, system, gcp, azure] timeout: 2s2. Monitoring the MonitorSet up alerting mechanisms on the collector's own metrics. By monitoring the health and performance of the collector itself, you can quickly identify issues before they affect your overall observability stack.3. Graceful DegradationConfigure timeout and retry policies for exporters to ensure that transient issues don’t lead to data loss. Implementing these policies allows the system to handle temporary failures gracefully without impacting the overall monitoring setup.exporters: otlp: endpoint: ${OTLP_ENDPOINT} tls: insecure: ${OTLP_INSECURE} timeout: 10s retry_on_failure: enabled: true attempts: 3 interval: 5s4. Versioning and UpgradesRegularly update the OpenTelemetry Collector to leverage the latest features, improvements, and bug fixes. Always test new versions in a staging environment before rolling them out to production to ensure compatibility with your existing setup.5. Configuration ManagementMaintain a version-controlled repository for your configuration files. This allows for easier tracking of changes, rollbacks when necessary, and collaboration across teams.Reliable Observability for 25+ million concurrent live-streaming viewers | Last9How we’ve tackled high cardinality metrics with long-term retention for one of the largest video streaming companies.Download PDFConclusionGetting a handle on host metrics monitoring with OpenTelemetry is like having a roadmap for your system’s performance. With the right setup, you’ll not only collect valuable data but also gain insights that can help you make smarter decisions about your infrastructure.🤝If you’re still eager to chat or have questions, our community on Discord is open. We’ve got a dedicated channel where you can have discussions with other developers about your specific use case.FAQsWhat does an OpenTelemetry Collector do?The OpenTelemetry Collector is like a central hub for telemetry data. It receives, processes, and exports logs, metrics, and traces from various sources, making it easier to monitor and analyze your systems without being tied to a specific vendor.What are host metrics?Host metrics are performance indicators that give you a glimpse into how your server is doing. They include things like CPU utilization, memory usage, disk space availability, network throughput, and the CPU usage of individual processes. These metrics are essential for keeping an eye on resource utilization and ensuring your infrastructure runs smoothly.What is the difference between telemetry and OpenTelemetry?Telemetry is the general term for collecting and sending data from remote sources to a system for monitoring and analysis. OpenTelemetry, on the other hand, is a specific framework with APIs designed for generating, collecting, and exporting telemetry data—logs, metrics, and traces—in a standardized way. It provides developers with the tools to instrument their applications effectively.Is the OpenTelemetry Collector observable?Absolutely! The OpenTelemetry Collector is observable itself. It generates its own telemetry data, such as metrics and logs, that you can monitor to evaluate its performance and health. This includes tracking things like resource usage, processing latency, and error rates, ensuring it operates effectively.What is the difference between OpenTelemetry Collector and Prometheus?While both are important in observability, they play different roles. The OpenTelemetry Collector acts as a data pipeline, collecting, processing, and exporting telemetry data. Prometheus is a monitoring and alerting toolkit specifically designed for storing and querying time-series data. You can scrape metrics from the OpenTelemetry Collector using Prometheus, and the collector can also export metrics directly to Prometheus.How do you configure the OpenTelemetry Collector to monitor host metrics?To configure the OpenTelemetry Collector for host metrics monitoring, set up a hostmetrics receiver in the configuration file. Specify the collection interval and the types of metrics you want to collect (like CPU, memory, disk, and network). Then, configure processors and exporters to handle and send the collected data to your chosen monitoring platform.How do you set up HostMetrics monitoring with the OpenTelemetry Collector?Setting up HostMetrics monitoring is straightforward. Create a configuration file that includes the HostMetrics receiver, define the metrics you want to collect, and specify an exporter to send the data to your monitoring solution (like Prometheus). Once your configuration is ready, start the collector with the file you created.Subscribe
Prometheus RemoteWrite Exporter: A Comprehensive Guide | Last9
A comprehensive guide showing how to use PrometheusRemoteWriteExporter to send metrics from OpenTelemetry to Prometheus compatible backends
 Table of Contents IntroductionPrometheus Remote Write Exporter: An OverviewConfiguring PrometheusRemoteWriteExporter in OpenTelemetryIntegration with Kubernetes and DockerAdvanced Configurations and Best PracticesTroubleshooting and Common IssuesFuture Trends and DevelopmentsConclusion 1. IntroductionOpenTelemetry (OTel) is an open-source framework that helps collect and manage telemetry data for observability. A crucial part of this framework is the PrometheusRemoteWriteExporter, which connects OpenTelemetry to the Prometheus ecosystem. In this post, we'll look at how the PrometheusRemoteWriteExporter works, how to configure it, and how it integrates with different observability tools.2. PrometheusRemoteWriteExporter: An OverviewThe PrometheusRemoteWriteExporter is a component of the OpenTelemetry Collector that allows you to export metrics data in the Prometheus remote write format. This exporter is particularly useful when sending OpenTelemetry metrics to Prometheus-compatible backends that support the remote write API, such as Last9, Cortex, Thanos, or even Grafana Cloud.Key features of the PrometheusRemoteWriteExporter include:Support for all OpenTelemetry metric types (gauge, sum, histogram, summary)Configurable endpoint for remote writeOptional TLS and authentication supportCustomizable headers for HTTP requestsAbility to add Prometheus-specific metadata to metricsNormalization of Metric names from OpenTelemetry naming convention to Prometheus-compatible naming conventionsDropping Delta temporality metrics before sending them to Prometheus-compatible backends.A significant advantage of using the PrometheusRemoteWriteExporter is that it lets you take advantage of OpenTelemetry's flexible instrumentation while still utilizing the monitoring and alerting tools you're used to with Prometheus. This is especially helpful if you're moving from Prometheus to OpenTelemetry or have a setup that uses both.3. Configuring PrometheusRemoteWriteExporter in OpenTelemetryTo set up the PrometheusRemoteWriteExporter in your OpenTelemetry Collector, you must add it to your collector's configuration file, usually in YAML format. Here’s a basic example of how to do this:exporters: prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" tls: insecure: true headers: "Authorization": "Basic <base64-encoded-credentials>" namespace: "my_app" resource_to_telemetry_conversion: enabled: true service: pipelines: metrics: receivers: [otlp] processors: [batch] exporters: [prometheusremotewrite]Let’s break down the critical configuration options:endpoint: This is the URL for your Prometheus-compatible backend, such as Last9 which supports Prometheus remote write protocol.tls: This section is for secure connections (optional).headers: Here, you can add any necessary HTTP headers, like authentication details.namespace: This optional prefix is added to all metric names.resource_to_telemetry_conversion: This option lets you convert all the resource attributes into metric labels. Default is false. This can increase high cardinality if the resource attributes, such as host names or IP addresses.In the service section, we define a pipeline that receives OTLP metrics, processes them in batches, and exports them using the PrometheusRemoteWriteExporter.The OpenTelemetry Collector (often called otel-collector) can also be set up to receive metrics in different formats, including the Prometheus exposition format. You’ll use the Prometheus receiver, which scrapes metrics from targets like a Prometheus server would. Here’s an example of how to configure the Prometheus receiver:receivers: prometheus: config: scrape_configs: - job_name: 'otel-collector' scrape_interval: 10s static_configs: - targets: ['0.0.0.0:8888'] service: pipelines: metrics: receivers: [prometheus] exporters: [prometheusremotewrite]With this setup, the OpenTelemetry Collector can scrape Prometheus metrics and export them using the PrometheusRemoteWriteExporter. This effectively creates a bridge between applications instrumented with Prometheus and Prometheus-compatible backends using OpenTelemetry Collector.4. Integration with Kubernetes and DockerIn cloud-native environments, applications are often run in containers orchestrated by Kubernetes. The PrometheusRemoteWriteExporter can effectively collect and export metrics from applications in these environments.Kubernetes IntegrationWhen deploying the OpenTelemetry Collector in a Kubernetes cluster, you can use the Kubernetes API server's service discovery mechanisms to discover and scrape metrics from your pods automatically. Here's an example of how you might configure this:receivers: prometheus: config: scrape_configs: - job_name: 'kubernetes-pods' kubernetes_sd_configs: - role: pod relabel_configs: - source_labels: [__meta_kubernetes_pod_annotation_prometheus_io_scrape] action: keep regex: true - source_labels: [__meta_kubernetes_pod_annotation_prometheus_io_path] action: replace target_label: __metrics_path__ regex: (.+) exporters: prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" service: pipelines: metrics: receivers: [prometheus] exporters: [prometheusremotewrite]This configuration uses Kubernetes service discovery to find pods annotated with prometheus.io/scrape: "true" and scrape metrics from them. The metrics are then exported using the PrometheusRemoteWriteExporter.Docker IntegrationFor Docker environments, you can run the OpenTelemetry Collector as a sidecar container alongside your application. This allows you to collect metrics from your application container and export them using the PrometheusRemoteWriteExporter. Here's a simple Docker Compose example:services: app: image: your-app-image ports: - "8080:8080" otel-collector: image: otel/opentelemetry-collector command: ["--config=/etc/otel-collector-config.yaml"] volumes: - ./otel-collector-config.yaml:/etc/otel-collector-config.yaml ports: - "8888:8888" # Prometheus metrics exporter - "8889:8889" # Prometheus exporter for the collectorIn this setup, you would configure your application to send metrics to the OpenTelemetry Collector, using the PrometheusRemoteWriteExporter to send the metrics to your Prometheus-compatible backend.5. Advanced Configurations and Best PracticesWhen working with the PrometheusRemoteWriteExporter, consider these advanced configurations and best practices:Use appropriate filtersThe OpenTelemetry Collector supports various processors that filter or transform metrics before exporting. This can reduce the volume of data sent to your Prometheus backend.processors: filter/metrics: error_mode: ignore metrics: metric: - 'name == "http.requests.total" and resource.attributes["env"] == "dev"' - 'type == METRIC_DATA_TYPE_HISTOGRAM' datapoint: - 'metric.type == METRIC_DATA_TYPE_SUMMARY' - 'resource.attributes["service.name"] == "user-service"'Implement retries and backoffConfigure the exporter to handle network issues gracefully:exporters: prometheusremotewrite: retry_on_failure: enabled: true # (default = true) initial_interval: 5s # Time to wait after the first failure before retrying; ignored if enabled is false max_interval: 30s # Is the upper bound on backoff; ignored if enabled is false max_elapsed_time: 120s # Is the maximum amount of time spent trying to send a batch; ignored if enabled is false. If set to 0, the retries are never stopped.Monitor the exporter Use the built-in metrics provided by the OpenTelemetry Collector to monitor the health and performance of your PrometheusRemoteWriteExporter. Update the service section of the Otel Collector config with detailed metrics.service: telemetry: metrics: level: "detailed"Use resource detection processorsThese can automatically detect and add relevant metadata about your environment:processors: resourcedetection: detectors: [env, ec2] timeout: 2s6. Troubleshooting and Common IssuesConnectivity issues: Ensure that the OpenTelemetry Collector can reach the Prometheus backend. Check network configurations, firewalls, and security groups.Authentication errors: Verify that the authentication credentials are correctly encoded in the configuration.Data type mismatches: The PrometheusRemoteWriteExporter may sometimes struggle with certain OpenTelemetry metric types. Check the OpenTelemetry Collector logs for any conversion errors.High cardinality: Be cautious of high cardinality metrics, which can overwhelm Prometheus. If necessary, use the metrics transform processor to reduce cardinality. Alternatively, you can use high cardinality metric backends such as Last9.To aid in troubleshooting, you can enable debug logging in the OpenTelemetry Collector:service: telemetry: logs: level: debug You can also use the debug exporter alongside the PrometheusRemoteWriteExporter to log the metrics being sent:exporters: debug: verbosity: detailed prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" service: pipelines: metrics: receivers: [otlp] processors: [batch] exporters: [logging, prometheusremotewrite]This configuration will log the metrics before they're sent to Prometheus, allowing you to verify the exported data. You can optionally enable the debug exporter when needed.7. Future Trends and DevelopmentsAs observability continues to evolve, several trends are shaping the future of tools like the PrometheusRemoteWriteExporter:Support for delta temporality metrics: As Prometheus 3.0 prepares to support OpenTelemetry metrics, the PrometheusRemoteWrite Exporter can pass delta metrics to Prometheus in the future.Support for Prometheus Remote Write 2.0 Protocol: Prometheus team is developing a new Prometheus 2.0 Protocol which was discussed in detail at PromCon 2024.Improved Performance: Ongoing efforts aim to optimize the performance of the PrometheusRemoteWriteExporter, especially for high-volume metric streams.Enhanced Resource Metadata Support: Improvements in handling and transmitting resource metadata and contextual information alongside metrics data are anticipated.8. ConclusionThe PrometheusRemoteWriteExporter in OpenTelemetry is crucial for connecting the OpenTelemetry framework with Prometheus-compatible backends.When building your observability strategy, focus on the best practices discussed here. Stay informed about new developments in the OpenTelemetry and Prometheus communities, and consider contributing your insights to these open-source projects.If you still need to discuss some settings, jump onto the Last9 Discord Server to discuss any specifics you need help with. We have a dedicated channel where you can discuss your specific use case with other developers.FAQsWhat is the difference between OpenTelemetry and Prometheus? Both are open-source projects under the Cloud Native Computing Foundation (CNCF) but serve different roles in observability. OpenTelemetry is a framework for instrumenting applications and collecting telemetry data (metrics, logs, and traces) in a standardized way. In contrast, Prometheus is primarily a monitoring system and time-series database focused on metrics collection and analysis, using a pull-based model to scrape data from instrumented applications.What is the difference between telemetry and OpenTelemetry?Telemetry refers to the collection and transmission of data for monitoring, typically including metrics, logs, and traces in software systems. OpenTelemetry is a specific framework that standardizes how telemetry data is generated, collected, and exported, making it easier for developers to implement observability in their applications.What is the difference between OpenTelemetry and Grafana?OpenTelemetry focuses on collecting and exporting telemetry data, acting as the plumbing that delivers observability data to backend systems. Grafana, on the other hand, is a visualization platform that creates dashboards and analyzes data from various sources, including Prometheus. While OpenTelemetry handles data collection, Grafana is responsible for visualizing that data. What is the difference between OpenTelemetry and distributed tracing?OpenTelemetry is a comprehensive framework that supports metrics, logs, and traces, facilitating the generation and collection of all these telemetry types. Distributed tracing is a technique specifically for monitoring requests as they move through microservices, forming one of the critical components of observabilitySubscribe
Table of Contents IntroductionPrometheus Remote Write Exporter: An OverviewConfiguring PrometheusRemoteWriteExporter in OpenTelemetryIntegration with Kubernetes and DockerAdvanced Configurations and Best PracticesTroubleshooting and Common IssuesFuture Trends and DevelopmentsConclusion 1. IntroductionOpenTelemetry (OTel) is an open-source framework that helps collect and manage telemetry data for observability. A crucial part of this framework is the PrometheusRemoteWriteExporter, which connects OpenTelemetry to the Prometheus ecosystem. In this post, we'll look at how the PrometheusRemoteWriteExporter works, how to configure it, and how it integrates with different observability tools.2. PrometheusRemoteWriteExporter: An OverviewThe PrometheusRemoteWriteExporter is a component of the OpenTelemetry Collector that allows you to export metrics data in the Prometheus remote write format. This exporter is particularly useful when sending OpenTelemetry metrics to Prometheus-compatible backends that support the remote write API, such as Last9, Cortex, Thanos, or even Grafana Cloud.Key features of the PrometheusRemoteWriteExporter include:Support for all OpenTelemetry metric types (gauge, sum, histogram, summary)Configurable endpoint for remote writeOptional TLS and authentication supportCustomizable headers for HTTP requestsAbility to add Prometheus-specific metadata to metricsNormalization of Metric names from OpenTelemetry naming convention to Prometheus-compatible naming conventionsDropping Delta temporality metrics before sending them to Prometheus-compatible backends.A significant advantage of using the PrometheusRemoteWriteExporter is that it lets you take advantage of OpenTelemetry's flexible instrumentation while still utilizing the monitoring and alerting tools you're used to with Prometheus. This is especially helpful if you're moving from Prometheus to OpenTelemetry or have a setup that uses both.3. Configuring PrometheusRemoteWriteExporter in OpenTelemetryTo set up the PrometheusRemoteWriteExporter in your OpenTelemetry Collector, you must add it to your collector's configuration file, usually in YAML format. Here’s a basic example of how to do this:exporters: prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" tls: insecure: true headers: "Authorization": "Basic <base64-encoded-credentials>" namespace: "my_app" resource_to_telemetry_conversion: enabled: true service: pipelines: metrics: receivers: [otlp] processors: [batch] exporters: [prometheusremotewrite]Let’s break down the critical configuration options:endpoint: This is the URL for your Prometheus-compatible backend, such as Last9 which supports Prometheus remote write protocol.tls: This section is for secure connections (optional).headers: Here, you can add any necessary HTTP headers, like authentication details.namespace: This optional prefix is added to all metric names.resource_to_telemetry_conversion: This option lets you convert all the resource attributes into metric labels. Default is false. This can increase high cardinality if the resource attributes, such as host names or IP addresses.In the service section, we define a pipeline that receives OTLP metrics, processes them in batches, and exports them using the PrometheusRemoteWriteExporter.The OpenTelemetry Collector (often called otel-collector) can also be set up to receive metrics in different formats, including the Prometheus exposition format. You’ll use the Prometheus receiver, which scrapes metrics from targets like a Prometheus server would. Here’s an example of how to configure the Prometheus receiver:receivers: prometheus: config: scrape_configs: - job_name: 'otel-collector' scrape_interval: 10s static_configs: - targets: ['0.0.0.0:8888'] service: pipelines: metrics: receivers: [prometheus] exporters: [prometheusremotewrite]With this setup, the OpenTelemetry Collector can scrape Prometheus metrics and export them using the PrometheusRemoteWriteExporter. This effectively creates a bridge between applications instrumented with Prometheus and Prometheus-compatible backends using OpenTelemetry Collector.4. Integration with Kubernetes and DockerIn cloud-native environments, applications are often run in containers orchestrated by Kubernetes. The PrometheusRemoteWriteExporter can effectively collect and export metrics from applications in these environments.Kubernetes IntegrationWhen deploying the OpenTelemetry Collector in a Kubernetes cluster, you can use the Kubernetes API server's service discovery mechanisms to discover and scrape metrics from your pods automatically. Here's an example of how you might configure this:receivers: prometheus: config: scrape_configs: - job_name: 'kubernetes-pods' kubernetes_sd_configs: - role: pod relabel_configs: - source_labels: [__meta_kubernetes_pod_annotation_prometheus_io_scrape] action: keep regex: true - source_labels: [__meta_kubernetes_pod_annotation_prometheus_io_path] action: replace target_label: __metrics_path__ regex: (.+) exporters: prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" service: pipelines: metrics: receivers: [prometheus] exporters: [prometheusremotewrite]This configuration uses Kubernetes service discovery to find pods annotated with prometheus.io/scrape: "true" and scrape metrics from them. The metrics are then exported using the PrometheusRemoteWriteExporter.Docker IntegrationFor Docker environments, you can run the OpenTelemetry Collector as a sidecar container alongside your application. This allows you to collect metrics from your application container and export them using the PrometheusRemoteWriteExporter. Here's a simple Docker Compose example:services: app: image: your-app-image ports: - "8080:8080" otel-collector: image: otel/opentelemetry-collector command: ["--config=/etc/otel-collector-config.yaml"] volumes: - ./otel-collector-config.yaml:/etc/otel-collector-config.yaml ports: - "8888:8888" # Prometheus metrics exporter - "8889:8889" # Prometheus exporter for the collectorIn this setup, you would configure your application to send metrics to the OpenTelemetry Collector, using the PrometheusRemoteWriteExporter to send the metrics to your Prometheus-compatible backend.5. Advanced Configurations and Best PracticesWhen working with the PrometheusRemoteWriteExporter, consider these advanced configurations and best practices:Use appropriate filtersThe OpenTelemetry Collector supports various processors that filter or transform metrics before exporting. This can reduce the volume of data sent to your Prometheus backend.processors: filter/metrics: error_mode: ignore metrics: metric: - 'name == "http.requests.total" and resource.attributes["env"] == "dev"' - 'type == METRIC_DATA_TYPE_HISTOGRAM' datapoint: - 'metric.type == METRIC_DATA_TYPE_SUMMARY' - 'resource.attributes["service.name"] == "user-service"'Implement retries and backoffConfigure the exporter to handle network issues gracefully:exporters: prometheusremotewrite: retry_on_failure: enabled: true # (default = true) initial_interval: 5s # Time to wait after the first failure before retrying; ignored if enabled is false max_interval: 30s # Is the upper bound on backoff; ignored if enabled is false max_elapsed_time: 120s # Is the maximum amount of time spent trying to send a batch; ignored if enabled is false. If set to 0, the retries are never stopped.Monitor the exporter Use the built-in metrics provided by the OpenTelemetry Collector to monitor the health and performance of your PrometheusRemoteWriteExporter. Update the service section of the Otel Collector config with detailed metrics.service: telemetry: metrics: level: "detailed"Use resource detection processorsThese can automatically detect and add relevant metadata about your environment:processors: resourcedetection: detectors: [env, ec2] timeout: 2s6. Troubleshooting and Common IssuesConnectivity issues: Ensure that the OpenTelemetry Collector can reach the Prometheus backend. Check network configurations, firewalls, and security groups.Authentication errors: Verify that the authentication credentials are correctly encoded in the configuration.Data type mismatches: The PrometheusRemoteWriteExporter may sometimes struggle with certain OpenTelemetry metric types. Check the OpenTelemetry Collector logs for any conversion errors.High cardinality: Be cautious of high cardinality metrics, which can overwhelm Prometheus. If necessary, use the metrics transform processor to reduce cardinality. Alternatively, you can use high cardinality metric backends such as Last9.To aid in troubleshooting, you can enable debug logging in the OpenTelemetry Collector:service: telemetry: logs: level: debug You can also use the debug exporter alongside the PrometheusRemoteWriteExporter to log the metrics being sent:exporters: debug: verbosity: detailed prometheusremotewrite: endpoint: "http://prometheus.example.com:9090/api/v1/write" service: pipelines: metrics: receivers: [otlp] processors: [batch] exporters: [logging, prometheusremotewrite]This configuration will log the metrics before they're sent to Prometheus, allowing you to verify the exported data. You can optionally enable the debug exporter when needed.7. Future Trends and DevelopmentsAs observability continues to evolve, several trends are shaping the future of tools like the PrometheusRemoteWriteExporter:Support for delta temporality metrics: As Prometheus 3.0 prepares to support OpenTelemetry metrics, the PrometheusRemoteWrite Exporter can pass delta metrics to Prometheus in the future.Support for Prometheus Remote Write 2.0 Protocol: Prometheus team is developing a new Prometheus 2.0 Protocol which was discussed in detail at PromCon 2024.Improved Performance: Ongoing efforts aim to optimize the performance of the PrometheusRemoteWriteExporter, especially for high-volume metric streams.Enhanced Resource Metadata Support: Improvements in handling and transmitting resource metadata and contextual information alongside metrics data are anticipated.8. ConclusionThe PrometheusRemoteWriteExporter in OpenTelemetry is crucial for connecting the OpenTelemetry framework with Prometheus-compatible backends.When building your observability strategy, focus on the best practices discussed here. Stay informed about new developments in the OpenTelemetry and Prometheus communities, and consider contributing your insights to these open-source projects.If you still need to discuss some settings, jump onto the Last9 Discord Server to discuss any specifics you need help with. We have a dedicated channel where you can discuss your specific use case with other developers.FAQsWhat is the difference between OpenTelemetry and Prometheus? Both are open-source projects under the Cloud Native Computing Foundation (CNCF) but serve different roles in observability. OpenTelemetry is a framework for instrumenting applications and collecting telemetry data (metrics, logs, and traces) in a standardized way. In contrast, Prometheus is primarily a monitoring system and time-series database focused on metrics collection and analysis, using a pull-based model to scrape data from instrumented applications.What is the difference between telemetry and OpenTelemetry?Telemetry refers to the collection and transmission of data for monitoring, typically including metrics, logs, and traces in software systems. OpenTelemetry is a specific framework that standardizes how telemetry data is generated, collected, and exported, making it easier for developers to implement observability in their applications.What is the difference between OpenTelemetry and Grafana?OpenTelemetry focuses on collecting and exporting telemetry data, acting as the plumbing that delivers observability data to backend systems. Grafana, on the other hand, is a visualization platform that creates dashboards and analyzes data from various sources, including Prometheus. While OpenTelemetry handles data collection, Grafana is responsible for visualizing that data. What is the difference between OpenTelemetry and distributed tracing?OpenTelemetry is a comprehensive framework that supports metrics, logs, and traces, facilitating the generation and collection of all these telemetry types. Distributed tracing is a technique specifically for monitoring requests as they move through microservices, forming one of the critical components of observabilitySubscribe
Log Analytics 101: Everything You Need to Know | Last9
Get a clear understanding of log analytics—what it is, why it matters, and how it helps you keep your systems running efficiently by analyzing key data from your infrastructure.
 Log analytics is essential for IT operations, helping teams monitor systems and resolve issues efficiently. It provides key insights into system performance, error detection, and areas for improvement. For anyone managing applications or infrastructure, understanding log analysis is critical to maintaining the reliability and stability of systems.Let's break down what log analytics means and its role in keeping systems healthy and efficient.The Essence of Log AnalyticsLog analytics involves collecting and analyzing log data from IT systems, applications, and infrastructure. It helps teams understand system behavior, performance, and overall health. Unlike basic log management, which is about gathering and storing logs, log analytics adds deeper analysis, offering ways to identify patterns, visualize data, and gain actionable insights from logs.📖Check out our blog on Log Anything vs. Log Everything to understand the key differences and how to choose the best logging strategy for your needs.Why Log Analytics MattersAs systems become more complex and distributed, particularly with the increasing use of microservices and Kubernetes, the amount of log data can quickly become overwhelming. Without effective log analytics:Troubleshooting becomes a nightmarePerformance optimization is guessworkSecurity threats may go unnoticedUser experience issues can slip through the cracksLog analytics addresses these challenges by providing real-time insights, enabling proactive monitoring, and facilitating faster root-cause analysis of performance issues.Key Components of Log AnalyticsA robust log analytics solution typically includes:Key Components of Log AnalyticsData Ingestion: Collecting logs from various data sources, including applications, operating systems, and virtual machines.Indexing: Organizing log data for efficient querying, often using SQL-like languages.Search and Query: This allows you to find specific log entries and patterns.Visualization: Creating dashboards and graphs for easy interpretation of data analytics results.Alerting: Notifying you of important events or anomalies.Machine Learning: Identifying patterns and predicting issues through advanced pattern recognition techniques.📖You'll find our blog, The Developer’s Handbook to Centralized Logging, relatable as it covers essential tips for effective logging practices.Implementing Log Analytics: Let's look at how log analytics works in practice, drawing from both general best practices and real-world experiences.Data Collection:Set up log collectors for each component of your system, including Windows servers, Linux machines, and cloud resources.In a recent project, we used Azure Monitor agents to collect logs from our Azure resources and on-premises servers.Centralized Storage:Use a centralized platform to aggregate all your logs.Microsoft Azure provides Azure Log Analytics Workspace for this purpose, which integrates seamlessly with other Azure services.Querying:Use a powerful query language to search through your logs. Azure Log Analytics uses the Kusto Query Language (KQL). Here's an example:Kusto QueryAzureActivity | where TimeGenerated > ago(1h) | where OperationName has "Microsoft.Compute/virtualMachines" | summarize count() by OperationName, ResultType Visualization:Create dashboards to visualize key metrics and trends.Azure Portal provides built-in visualization tools, but you can also use popular options like Grafana for custom dashboards.Alerting:Set up alerts for specific error patterns and performance thresholds.Azure Monitor allows you to create actionable alerts based on log query results.Popular Log Analytics Tools and ProvidersThere are several excellent options in the market:Azure Monitor: Integrated with Azure services, great for monitoring Azure resources and hybrid environments.Elastic Stack (ELK): Open-source solution, suitable for on-premises deployments.Last9: A telemetry data warehouse that brings together metrics, logs, and traces in one unified platform, making it ideal for managing complex systems at scale.Splunk: Powerful enterprise-grade solution with advanced SIEM capabilities.Amazon CloudWatch: Integrated with AWS services, similar to Azure Monitor in the Azure ecosystem.Grafana Loki: Lightweight, Prometheus-inspired, great for Kubernetes workloads.Best Practices for Log AnalyticsBased on industry standards and my experiences, here are some tips to get the most out of your log analytics:Structure Your Logs: Use a consistent format (e.g., JSON) to make parsing easier.Include Contextual Information: Add trace IDs, user IDs, and other relevant metadata to your logs.Sample Wisely: In high-volume environments, implement intelligent sampling to reduce costs without losing important information.Automate: Set up automated alerts and dashboards to proactively monitor your systems.Retention Strategy: Define a clear retention policy based on your compliance and analytical needs.API Integration: Utilize APIs provided by log analytics tools to automate log ingestion and analysis processes.Use Cases for Log AnalyticsLog analytics has a wide range of applications across IT operations and security:Troubleshooting: Quickly identify the root cause of errors and performance issues.Performance Monitoring: Track system health, resource utilization, and application performance.Security Analysis: Detect and investigate security threats and anomalies.Compliance: Generate audit trails and reports for regulatory compliance.User Behavior Analysis: Understand how users interact with your applications to improve user experience.Capacity Planning: Analyze usage patterns to forecast future resource needs.📝For a practical take on logging in Golang, be sure to check out our blog on Golang Logging.Challenges in Log AnalyticsWhile log analytics is powerful, it's not without challenges:Data Volume: As systems grow, log data can become overwhelming, impacting storage and processing costs.Privacy Concerns: Logs may contain sensitive information, requiring careful handling and compliance with data protection regulations.Tool Complexity: Some log analytics tools have steep learning curves, requiring dedicated training and expertise.Analysis Paralysis: With so much data available, it's easy to get lost in the details and lose sight of key insights.ConclusionLog analytics is more than just a tool; it’s a smart approach to managing our systems. It helps troubleshoot issues, improve performance, and keep our environments secure.The goal is to go beyond merely collecting logs; it's about finding insights that can enhance your systems and processes.If you want a solution to manage metrics, traces, and logs all in one place, check out Last9. Schedule a demo with us to learn more, or start your free trial to explore the platform.🤝If you’re uncertain about which path to follow, consider joining our Discord community! We have a dedicated channel where you can share your specific use case and connect with other developers.FAQsWhat is meant by log analytics?Log analytics refers to the process of collecting, analyzing, and deriving insights from log data generated by various IT systems and applications.What is log analysis used for?Log analysis is used for troubleshooting, performance monitoring, security analysis, compliance reporting, and understanding user behavior.How does log analytics work in cloud computing environments?In cloud environments, log analytics tools collect data from various cloud resources, centralize it, and provide analysis and visualization capabilities, often integrating with other cloud services for comprehensive monitoring.How does log analytics differ from log management?Log management focuses on collecting, storing, and indexing log data, while log analytics goes a step further by analyzing and visualizing this data to identify trends, anomalies, and actionable insights.What types of log data are commonly analyzed?Commonly analyzed logs include application logs, system logs, network logs, security logs, and audit logs. Each provides different insights into the performance, security, and operations of IT systems.Can log analytics improve system security?Yes, log analytics can help detect security threats by analyzing patterns and anomalies in log data. It can be used to identify suspicious activity, track unauthorized access, and support incident investigations.How do you optimize log queries in log analytics?Optimizing log queries involves using the right filters, avoiding unnecessary data collection, aggregating data where possible, and leveraging tools that support efficient query processing, such as Azure Log Analytics or Splunk.What role does machine learning play in log analytics?Machine learning can be used in log analytics to identify patterns and predict potential issues. It helps with anomaly detection, trend analysis, and the automated identification of recurring problems.How does log analytics support compliance efforts?Log analytics assists with compliance by tracking and auditing system activity, providing reports that can demonstrate adherence to regulations such as GDPR, HIPAA, and PCI-DSS.Subscribe
Log analytics is essential for IT operations, helping teams monitor systems and resolve issues efficiently. It provides key insights into system performance, error detection, and areas for improvement. For anyone managing applications or infrastructure, understanding log analysis is critical to maintaining the reliability and stability of systems.Let's break down what log analytics means and its role in keeping systems healthy and efficient.The Essence of Log AnalyticsLog analytics involves collecting and analyzing log data from IT systems, applications, and infrastructure. It helps teams understand system behavior, performance, and overall health. Unlike basic log management, which is about gathering and storing logs, log analytics adds deeper analysis, offering ways to identify patterns, visualize data, and gain actionable insights from logs.📖Check out our blog on Log Anything vs. Log Everything to understand the key differences and how to choose the best logging strategy for your needs.Why Log Analytics MattersAs systems become more complex and distributed, particularly with the increasing use of microservices and Kubernetes, the amount of log data can quickly become overwhelming. Without effective log analytics:Troubleshooting becomes a nightmarePerformance optimization is guessworkSecurity threats may go unnoticedUser experience issues can slip through the cracksLog analytics addresses these challenges by providing real-time insights, enabling proactive monitoring, and facilitating faster root-cause analysis of performance issues.Key Components of Log AnalyticsA robust log analytics solution typically includes:Key Components of Log AnalyticsData Ingestion: Collecting logs from various data sources, including applications, operating systems, and virtual machines.Indexing: Organizing log data for efficient querying, often using SQL-like languages.Search and Query: This allows you to find specific log entries and patterns.Visualization: Creating dashboards and graphs for easy interpretation of data analytics results.Alerting: Notifying you of important events or anomalies.Machine Learning: Identifying patterns and predicting issues through advanced pattern recognition techniques.📖You'll find our blog, The Developer’s Handbook to Centralized Logging, relatable as it covers essential tips for effective logging practices.Implementing Log Analytics: Let's look at how log analytics works in practice, drawing from both general best practices and real-world experiences.Data Collection:Set up log collectors for each component of your system, including Windows servers, Linux machines, and cloud resources.In a recent project, we used Azure Monitor agents to collect logs from our Azure resources and on-premises servers.Centralized Storage:Use a centralized platform to aggregate all your logs.Microsoft Azure provides Azure Log Analytics Workspace for this purpose, which integrates seamlessly with other Azure services.Querying:Use a powerful query language to search through your logs. Azure Log Analytics uses the Kusto Query Language (KQL). Here's an example:Kusto QueryAzureActivity | where TimeGenerated > ago(1h) | where OperationName has "Microsoft.Compute/virtualMachines" | summarize count() by OperationName, ResultType Visualization:Create dashboards to visualize key metrics and trends.Azure Portal provides built-in visualization tools, but you can also use popular options like Grafana for custom dashboards.Alerting:Set up alerts for specific error patterns and performance thresholds.Azure Monitor allows you to create actionable alerts based on log query results.Popular Log Analytics Tools and ProvidersThere are several excellent options in the market:Azure Monitor: Integrated with Azure services, great for monitoring Azure resources and hybrid environments.Elastic Stack (ELK): Open-source solution, suitable for on-premises deployments.Last9: A telemetry data warehouse that brings together metrics, logs, and traces in one unified platform, making it ideal for managing complex systems at scale.Splunk: Powerful enterprise-grade solution with advanced SIEM capabilities.Amazon CloudWatch: Integrated with AWS services, similar to Azure Monitor in the Azure ecosystem.Grafana Loki: Lightweight, Prometheus-inspired, great for Kubernetes workloads.Best Practices for Log AnalyticsBased on industry standards and my experiences, here are some tips to get the most out of your log analytics:Structure Your Logs: Use a consistent format (e.g., JSON) to make parsing easier.Include Contextual Information: Add trace IDs, user IDs, and other relevant metadata to your logs.Sample Wisely: In high-volume environments, implement intelligent sampling to reduce costs without losing important information.Automate: Set up automated alerts and dashboards to proactively monitor your systems.Retention Strategy: Define a clear retention policy based on your compliance and analytical needs.API Integration: Utilize APIs provided by log analytics tools to automate log ingestion and analysis processes.Use Cases for Log AnalyticsLog analytics has a wide range of applications across IT operations and security:Troubleshooting: Quickly identify the root cause of errors and performance issues.Performance Monitoring: Track system health, resource utilization, and application performance.Security Analysis: Detect and investigate security threats and anomalies.Compliance: Generate audit trails and reports for regulatory compliance.User Behavior Analysis: Understand how users interact with your applications to improve user experience.Capacity Planning: Analyze usage patterns to forecast future resource needs.📝For a practical take on logging in Golang, be sure to check out our blog on Golang Logging.Challenges in Log AnalyticsWhile log analytics is powerful, it's not without challenges:Data Volume: As systems grow, log data can become overwhelming, impacting storage and processing costs.Privacy Concerns: Logs may contain sensitive information, requiring careful handling and compliance with data protection regulations.Tool Complexity: Some log analytics tools have steep learning curves, requiring dedicated training and expertise.Analysis Paralysis: With so much data available, it's easy to get lost in the details and lose sight of key insights.ConclusionLog analytics is more than just a tool; it’s a smart approach to managing our systems. It helps troubleshoot issues, improve performance, and keep our environments secure.The goal is to go beyond merely collecting logs; it's about finding insights that can enhance your systems and processes.If you want a solution to manage metrics, traces, and logs all in one place, check out Last9. Schedule a demo with us to learn more, or start your free trial to explore the platform.🤝If you’re uncertain about which path to follow, consider joining our Discord community! We have a dedicated channel where you can share your specific use case and connect with other developers.FAQsWhat is meant by log analytics?Log analytics refers to the process of collecting, analyzing, and deriving insights from log data generated by various IT systems and applications.What is log analysis used for?Log analysis is used for troubleshooting, performance monitoring, security analysis, compliance reporting, and understanding user behavior.How does log analytics work in cloud computing environments?In cloud environments, log analytics tools collect data from various cloud resources, centralize it, and provide analysis and visualization capabilities, often integrating with other cloud services for comprehensive monitoring.How does log analytics differ from log management?Log management focuses on collecting, storing, and indexing log data, while log analytics goes a step further by analyzing and visualizing this data to identify trends, anomalies, and actionable insights.What types of log data are commonly analyzed?Commonly analyzed logs include application logs, system logs, network logs, security logs, and audit logs. Each provides different insights into the performance, security, and operations of IT systems.Can log analytics improve system security?Yes, log analytics can help detect security threats by analyzing patterns and anomalies in log data. It can be used to identify suspicious activity, track unauthorized access, and support incident investigations.How do you optimize log queries in log analytics?Optimizing log queries involves using the right filters, avoiding unnecessary data collection, aggregating data where possible, and leveraging tools that support efficient query processing, such as Azure Log Analytics or Splunk.What role does machine learning play in log analytics?Machine learning can be used in log analytics to identify patterns and predict potential issues. It helps with anomaly detection, trend analysis, and the automated identification of recurring problems.How does log analytics support compliance efforts?Log analytics assists with compliance by tracking and auditing system activity, providing reports that can demonstrate adherence to regulations such as GDPR, HIPAA, and PCI-DSS.Subscribe
Log Anything vs Log Everything | Last9
Explore the logging spectrum from “Log Anything” chaos to “Log Everything” clarity. Learn structured logging best practices in Go with zap!
 Recently, I posted on LinkedIn about what I've observed in terms of logging practices across different teams. The post resonated with many developers, sparking discussions and suggestions. So, I thought it would be worthwhile to expand on this topic and share my opinions in more detail.As a developer who's spent countless hours knee-deep in logs, trying to decipher the cryptic messages left by past me (or my well-meaning colleagues), I've come to appreciate the art of effective logging. It's a journey from chaos to clarity, from frustration to insight. Let me take you through this journey, sharing what I've learned from working with various teams on the ground.The Logging SpectrumFrom "Log Anything" to "Log Everything".At one end, we have the "Log Anything" approach, and at the other, the "Log Everything" strategy. Let's break these down and see why moving towards the right end of the spectrum can save you (and your future self) from countless headaches and the best way to reach there.Log Anything: The Mystery Juice of LoggingWe've all been there, especially in the heat of debugging a particularly nasty bug. It usually looks something like this:console.log("here")print("Why isn't this working?!")logger.info("i = " + i)console.log("AAAAARGH!")An absolutely useful Python Logging Guide that shows how to do it right.This approach is like a mystery juice – it might be helpful, it might be useless, but you won't know until you're desperately trying to debug an issue at 3 AM. Here's why this approach falls short:Unstructured Chaos: Random console.log() or print() statements scattered throughout your code make it nearly impossible to parse or analyze logs systematically.Contextless Noise: Logs like "here" or "AAAAARGH!" might have meant something to you when you wrote them, but good luck deciphering that during a production incident.Inconsistent Severity: When everything is logged at the same level, nothing stands out. It's like trying to find a specific drop of water in a waterfall.Future You Will Curse Past You: Trust me, I've been there. You'll be debugging an issue, come across these logs, and wonder what on earth you were thinking.Log Everything: The Fine Wine of LoggingDon't let the name fool you – it's not about logging literally everything, but rather about logging thoughtfully and consistently. This is the fine wine of logging – complex yet clear, and it only gets better with time.Here's what "Log Everything" looks like in practice:Structured, Consistent Logging look similar tologger.info("User action", extra={ "user_id": user.id, "action": "login", "ip_address": request.ip, "timestamp": datetime.utcnow().isoformat()})💡Golang - its tricky to do this I know. I wrote a Golang logging guide for that very purpose. Its fun to run into your own blogpost when doing a google searchHigh-Cardinality Data: Include relevant context that will help you understand the state of your system when the log was created.Events That Tell a Story: Log the journey of a request or a user action through your system.Thoughtful Severity Levels: Use appropriate log levels (DEBUG, INFO, WARNING, ERROR, CRITICAL) consistently across your services.The Payoff: Why "Log Everything" WinsFaster Debugging: With contextual information readily available, you can quickly narrow down issues.Better Insights: Structured logs can be easily parsed and analyzed, giving you insights into system behavior over time.Proactive Problem Solving: With comprehensive logging, you can often spot issues before they become critical failures.Happier Future You: Trust me, you'll thank yourself when you're able to resolve issues quickly, even at 3 AM.Implementing "Log Everything" in Your ProjectUse a Logging Framework: Utilize robust logging libraries like Python's logging module, or more advanced options like structlog for Python or winston for Node.js.Define Log Levels: Establish clear guidelines for when to use each log level (DEBUG, INFO, WARNING, ERROR, CRITICAL).Structured Logging: Use JSON or another structured format for your logs. This makes them easy to parse and analyze.Include Context: Always include relevant contextual information like user IDs, request IDs, and timestamps.Log Life Cycles: Track the journey of important operations through your system.Use Log Aggregation Tools: Implement tools like Last9, Loki or Splunk to centralize and analyze your logs. 💡Last9 has a very nifty feature to turn your logs into a structured format at INGESTION instead of having to go back and changing instrumentation.Striking the Right BalanceWhile the "Log Everything" approach is generally superior, it's crucial to strike the right balance. Over-logging can lead to performance issues and make it harder to find relevant information. Here are some tips to find that sweet spot:Be Selective: Log important events and state changes, not every minor detail.Use Log Levels Wisely: Reserve ERROR for actual errors, use INFO for normal operations, and DEBUG for detailed information useful during development.Rotate and Retain: Implement log rotation and retention policies to manage storage and maintain performance.Sample High-Volume Events: For high-volume events, consider sampling a percentage of logs rather than logging every single occurrence.Leverage Feature Flags: Use feature flags to dynamically adjust logging verbosity in production when needed for troubleshooting.Log to Metrics: Using Last9's streaming aggregations - you can turn logs into metrics at ingestion that allows for better control and alerting downstreamConclusionRemember, the goal isn't to drown in data but to create a clear, structured narrative of your system's behavior. By moving from "Log Anything" to "Log Everything," you're not just helping the future; you're creating a more observable, debuggable, and ultimately more reliable system.So, the next time you're tempted to throw in a quick console.log("here"), take a moment to think about what future you at 3 AM might need to know. Your future self will thank you, and you might just find that debugging becomes less of a dreaded chore and more of an insightful journey through your application's story.Happy logging, and may your debugging sessions be short and your insights be plentiful!Subscribe
Recently, I posted on LinkedIn about what I've observed in terms of logging practices across different teams. The post resonated with many developers, sparking discussions and suggestions. So, I thought it would be worthwhile to expand on this topic and share my opinions in more detail.As a developer who's spent countless hours knee-deep in logs, trying to decipher the cryptic messages left by past me (or my well-meaning colleagues), I've come to appreciate the art of effective logging. It's a journey from chaos to clarity, from frustration to insight. Let me take you through this journey, sharing what I've learned from working with various teams on the ground.The Logging SpectrumFrom "Log Anything" to "Log Everything".At one end, we have the "Log Anything" approach, and at the other, the "Log Everything" strategy. Let's break these down and see why moving towards the right end of the spectrum can save you (and your future self) from countless headaches and the best way to reach there.Log Anything: The Mystery Juice of LoggingWe've all been there, especially in the heat of debugging a particularly nasty bug. It usually looks something like this:console.log("here")print("Why isn't this working?!")logger.info("i = " + i)console.log("AAAAARGH!")An absolutely useful Python Logging Guide that shows how to do it right.This approach is like a mystery juice – it might be helpful, it might be useless, but you won't know until you're desperately trying to debug an issue at 3 AM. Here's why this approach falls short:Unstructured Chaos: Random console.log() or print() statements scattered throughout your code make it nearly impossible to parse or analyze logs systematically.Contextless Noise: Logs like "here" or "AAAAARGH!" might have meant something to you when you wrote them, but good luck deciphering that during a production incident.Inconsistent Severity: When everything is logged at the same level, nothing stands out. It's like trying to find a specific drop of water in a waterfall.Future You Will Curse Past You: Trust me, I've been there. You'll be debugging an issue, come across these logs, and wonder what on earth you were thinking.Log Everything: The Fine Wine of LoggingDon't let the name fool you – it's not about logging literally everything, but rather about logging thoughtfully and consistently. This is the fine wine of logging – complex yet clear, and it only gets better with time.Here's what "Log Everything" looks like in practice:Structured, Consistent Logging look similar tologger.info("User action", extra={ "user_id": user.id, "action": "login", "ip_address": request.ip, "timestamp": datetime.utcnow().isoformat()})💡Golang - its tricky to do this I know. I wrote a Golang logging guide for that very purpose. Its fun to run into your own blogpost when doing a google searchHigh-Cardinality Data: Include relevant context that will help you understand the state of your system when the log was created.Events That Tell a Story: Log the journey of a request or a user action through your system.Thoughtful Severity Levels: Use appropriate log levels (DEBUG, INFO, WARNING, ERROR, CRITICAL) consistently across your services.The Payoff: Why "Log Everything" WinsFaster Debugging: With contextual information readily available, you can quickly narrow down issues.Better Insights: Structured logs can be easily parsed and analyzed, giving you insights into system behavior over time.Proactive Problem Solving: With comprehensive logging, you can often spot issues before they become critical failures.Happier Future You: Trust me, you'll thank yourself when you're able to resolve issues quickly, even at 3 AM.Implementing "Log Everything" in Your ProjectUse a Logging Framework: Utilize robust logging libraries like Python's logging module, or more advanced options like structlog for Python or winston for Node.js.Define Log Levels: Establish clear guidelines for when to use each log level (DEBUG, INFO, WARNING, ERROR, CRITICAL).Structured Logging: Use JSON or another structured format for your logs. This makes them easy to parse and analyze.Include Context: Always include relevant contextual information like user IDs, request IDs, and timestamps.Log Life Cycles: Track the journey of important operations through your system.Use Log Aggregation Tools: Implement tools like Last9, Loki or Splunk to centralize and analyze your logs. 💡Last9 has a very nifty feature to turn your logs into a structured format at INGESTION instead of having to go back and changing instrumentation.Striking the Right BalanceWhile the "Log Everything" approach is generally superior, it's crucial to strike the right balance. Over-logging can lead to performance issues and make it harder to find relevant information. Here are some tips to find that sweet spot:Be Selective: Log important events and state changes, not every minor detail.Use Log Levels Wisely: Reserve ERROR for actual errors, use INFO for normal operations, and DEBUG for detailed information useful during development.Rotate and Retain: Implement log rotation and retention policies to manage storage and maintain performance.Sample High-Volume Events: For high-volume events, consider sampling a percentage of logs rather than logging every single occurrence.Leverage Feature Flags: Use feature flags to dynamically adjust logging verbosity in production when needed for troubleshooting.Log to Metrics: Using Last9's streaming aggregations - you can turn logs into metrics at ingestion that allows for better control and alerting downstreamConclusionRemember, the goal isn't to drown in data but to create a clear, structured narrative of your system's behavior. By moving from "Log Anything" to "Log Everything," you're not just helping the future; you're creating a more observable, debuggable, and ultimately more reliable system.So, the next time you're tempted to throw in a quick console.log("here"), take a moment to think about what future you at 3 AM might need to know. Your future self will thank you, and you might just find that debugging becomes less of a dreaded chore and more of an insightful journey through your application's story.Happy logging, and may your debugging sessions be short and your insights be plentiful!Subscribe
Docker Monitoring with Prometheus: A Step-by-Step Guide | Last9
This guide walks you through setting up Docker monitoring using Prometheus and Grafana, helping you track container performance and resource usage with ease.
 In today’s containerized world, Docker has become a must-have tool for DevOps teams. But with the flexibility and efficiency of containers comes the need for effective monitoring.In this tutorial, we’ll walk you through how to set up a reliable monitoring solution for your Docker containers using Prometheus, an open-source toolkit for monitoring and alerting, along with Grafana for visualizing your data. This setup is great for various environments, including Linux distributions like Ubuntu, and can easily be adapted for cloud platforms like AWS.PrerequisitesBefore we begin, ensure you have the following installed on your system:DockerDocker ComposeBasic knowledge of YAML and JSON filesWhy Monitor Docker Containers?Monitoring Docker containers is crucial for several reasons:Performance optimization: (CPU and memory usage)Resource allocationTroubleshootingCapacity planningEnsuring high availabilitySetting Up Prometheus for Docker MonitoringLet's start by setting up Prometheus to collect metrics from our Docker environment.Step 1: Create a Docker Compose FileCreate a file named docker-compose.yml with the following content:version: '3'services: prometheus: image: prom/prometheus:latest container_name: prometheus ports: - 9090:9090 volumes: - ./prometheus.yml:/etc/prometheus/prometheus.yml - prometheus_data:/prometheus command: - '--config.file=/etc/prometheus/prometheus.yml' - '--storage.tsdb.path=/prometheus' - '--web.console.libraries=/usr/share/prometheus/console_libraries' - '--web.console.templates=/usr/share/prometheus/consoles' cadvisor: image: gcr.io/cadvisor/cadvisor:latest container_name: cadvisor ports: - 8080:8080 volumes: - /:/rootfs:ro - /var/run:/var/run:rw - /sys:/sys:ro - /var/lib/docker/:/var/lib/docker:ro node-exporter: image: prom/node-exporter:latest container_name: node-exporter ports: - 9100:9100 volumes: - /proc:/host/proc:ro - /sys:/host/sys:ro - /:/rootfs:ro command: - '--path.procfs=/host/proc' - '--path.sysfs=/host/sys' - '--collector.filesystem.ignored-mount-points="^/(sys|proc|dev|host|etc)($$|/)"' volumes: prometheus_data: {}This compose file sets up three services:Prometheus: The main monitoring service.cAdvisor: For collecting container metrics.Node Exporter: For collecting host metrics.Step 2: Create Prometheus ConfigurationCreate a file named prometheus.yml with the following content:global: scrape_interval: 15sscrape_configs: - job_name: 'prometheus' static_configs: - targets: ['localhost:9090'] - job_name: 'cadvisor' static_configs: - targets: ['cadvisor:8080'] - job_name: 'node-exporter' static_configs: - targets: ['node-exporter:9100']This configuration file tells Prometheus where to scrape metrics from, including the Prometheus server itself.Step 3: Start the ServicesRun the following command to start the services:docker-compose up -dThis command will pull the necessary images and start the containers in detached mode.Setting Up Grafana for VisualizationNow that we have Prometheus collecting metrics, let's set up Grafana for visualization.Step 4: Add Grafana to Docker ComposeUpdate your docker-compose.yml file to include Grafana:grafana: image: grafana/grafana:latest container_name: grafana ports: - 3000:3000 volumes: - grafana_data:/var/lib/grafana environment: - GF_SECURITY_ADMIN_PASSWORD=adminvolumes: grafana_data: {}Step 5: Restart the ServicesRun the following command to apply the changes:docker-compose up -dStep 6: Configure GrafanaOpen a web browser and navigate to http://localhost:3000.Log in with the username admin and password admin.Go to Configuration > Data Sources.Add a new Prometheus data source.Set the URL to http://prometheus:9090.Click Save & Test.Step 7: Import DashboardsGrafana has many pre-built dashboards for Docker monitoring. You can import them using the following steps:Go to Create > Import.Enter the dashboard ID (e.g., 893 for Docker and system monitoring).Select your Prometheus data source.Click Import.These dashboards will provide graphs and visualizations for various metrics, including CPU and memory usage of your running containers.Prometheus Recording Rules: A Developer’s Guide to Query Optimization | Last9This guide breaks down how recording rules can help, with simple tips to improve performance and manage complex data.Book a DemoBook a DemoMonitoring Docker Containers in ProductionFor production environments, consider the following best practices:Use alerting: Set up Alertmanager to notify you of critical issues such as high resource usage or service downtimes.Implement security measures: Ensure proper authentication and encryption to secure your monitoring stack.Scale your monitoring: If your infrastructure grows, consider using remote storage solutions for long-term metric retention.Monitor the monitors: Keep an eye on the health of your monitoring tools themselves to ensure they are functioning properly.Monitoring Docker DaemonTo monitor the Docker daemon itself, you can use the Docker Engine metrics endpoint. Add the following to your prometheus.yml configuration file:- job_name: 'docker' static_configs: - targets: ['docker-host:9323']Make sure to replace docker-host with the appropriate IP address or hostname of your Docker host.Next, configure the Docker daemon to expose metrics by editing the /etc/docker/daemon.json file:{ "metrics-addr": "0.0.0.0:9323", "experimental": true}Restart the Docker daemon for these changes to take effect.High Availability in Prometheus: Best Practices and Tips | Last9This blog defines high availability in Prometheus, discusses challenges, and offers essential tips for reliable monitoring in cloud-native environments.Book a DemoBook a DemoAdvanced Monitoring TechniquesMonitoring Nginx with PrometheusIf you're running Nginx within your Docker environment, you can monitor it using the Nginx Prometheus Exporter. To set this up, add the following to your docker-compose.yml:nginx-exporter: image: nginx/nginx-prometheus-exporter:latest command: - '-nginx.scrape-uri=http://nginx:8080/stub_status' ports: - 9113:9113Then, add a new job to your prometheus.yml configuration file:- job_name: 'nginx' static_configs: - targets: ['nginx-exporter:9113']Kubernetes IntegrationIf you are using Kubernetes, you can adapt this monitoring setup by employing the Prometheus Operator, which automates the deployment and configuration of Prometheus in a Kubernetes cluster. The operator enables automatic discovery and monitoring of pods, services, and nodes within your cluster.Time Series Data and Backend StoragePrometheus is highly efficient in storing time series data, which allows for fast querying and analysis of metrics. However, for long-term storage, especially in larger environments, it is advisable to use remote storage solutions capable of handling extensive time series data.Automation and ProvisioningTo simplify and expedite the setup process, you can create scripts or utilize configuration management tools (e.g., Ansible or Terraform) to automate the deployment of your monitoring stack. This is especially useful when provisioning new environments or scaling your infrastructure.Plugins and ExtensionsGrafana supports a wide range of plugins that can extend its functionality. For example, the AWS CloudWatch plugin allows you to integrate metrics from AWS services alongside your Docker metrics, providing a comprehensive monitoring solution for hybrid environments.ConclusionMonitoring Docker containers with Prometheus and Grafana gives you valuable insights into the health and performance of your applications. As your infrastructure grows, it’s a good idea to revisit and fine-tune your monitoring setup to make sure everything runs smoothly. There are plenty of open-source projects on GitHub where you can explore different configurations and examples to suit your needs.Whether you’re running a small dev environment or managing a large production system, keeping an eye on your containers is key to maintaining reliability. If you have any questions or want to discuss this further, feel free to get in touch, or join our Discord community where developers like you are always sharing tips and advice.Good luck with your setup, and happy monitoring!FAQsHow do I monitor my Docker containers?You can monitor Docker containers by using tools like Prometheus and Grafana. Prometheus collects metrics from containers, while Grafana helps visualize them. Additionally, Docker’s built-in command-line tools like docker stats allow real-time resource monitoring of CPU, memory, and network usage.How do I use Prometheus and Grafana in Docker?To use Prometheus and Grafana in Docker, you can set them up using Docker Compose. Prometheus collects container metrics, while Grafana visualizes the data. Simply configure a docker-compose.yml file to include Prometheus, Grafana, and cAdvisor to gather container metrics.How do I monitor Docker containers in production?Monitoring Docker containers in production involves setting up Prometheus for metrics collection and using Alertmanager for notifications. Security and scalability are critical, so ensure secure authentication, and consider long-term storage for metrics. Remote storage options can help manage large datasets effectively.How do I monitor Docker daemon?To monitor the Docker daemon, you can expose Docker Engine metrics by configuring the Docker daemon to use the /metrics endpoint. Prometheus can then scrape these metrics by adding the Docker host's IP address and port to the Prometheus configuration file.What are the benefits of monitoring Docker containers?Monitoring Docker containers helps optimize performance, allocate resources, troubleshoot issues, plan for capacity, and ensure high availability. It provides insights into CPU, memory, and network usage, helping you maintain the health and performance of your applications.What is the difference between Docker monitoring and container monitoring?Docker monitoring specifically focuses on monitoring Docker containers and the Docker Engine, while container monitoring generally refers to tracking the performance of any containerized environment, regardless of the container runtime used, such as Docker, CRI-O, or containerd.How do I monitor a Docker container using Prometheus?You can monitor a Docker container using Prometheus by setting up cAdvisor or Node Exporter to gather metrics. Prometheus scrapes these metrics from your Docker environment, which can then be visualized in Grafana for better insights into container performance.SubscribeBook a Demo
In today’s containerized world, Docker has become a must-have tool for DevOps teams. But with the flexibility and efficiency of containers comes the need for effective monitoring.In this tutorial, we’ll walk you through how to set up a reliable monitoring solution for your Docker containers using Prometheus, an open-source toolkit for monitoring and alerting, along with Grafana for visualizing your data. This setup is great for various environments, including Linux distributions like Ubuntu, and can easily be adapted for cloud platforms like AWS.PrerequisitesBefore we begin, ensure you have the following installed on your system:DockerDocker ComposeBasic knowledge of YAML and JSON filesWhy Monitor Docker Containers?Monitoring Docker containers is crucial for several reasons:Performance optimization: (CPU and memory usage)Resource allocationTroubleshootingCapacity planningEnsuring high availabilitySetting Up Prometheus for Docker MonitoringLet's start by setting up Prometheus to collect metrics from our Docker environment.Step 1: Create a Docker Compose FileCreate a file named docker-compose.yml with the following content:version: '3'services: prometheus: image: prom/prometheus:latest container_name: prometheus ports: - 9090:9090 volumes: - ./prometheus.yml:/etc/prometheus/prometheus.yml - prometheus_data:/prometheus command: - '--config.file=/etc/prometheus/prometheus.yml' - '--storage.tsdb.path=/prometheus' - '--web.console.libraries=/usr/share/prometheus/console_libraries' - '--web.console.templates=/usr/share/prometheus/consoles' cadvisor: image: gcr.io/cadvisor/cadvisor:latest container_name: cadvisor ports: - 8080:8080 volumes: - /:/rootfs:ro - /var/run:/var/run:rw - /sys:/sys:ro - /var/lib/docker/:/var/lib/docker:ro node-exporter: image: prom/node-exporter:latest container_name: node-exporter ports: - 9100:9100 volumes: - /proc:/host/proc:ro - /sys:/host/sys:ro - /:/rootfs:ro command: - '--path.procfs=/host/proc' - '--path.sysfs=/host/sys' - '--collector.filesystem.ignored-mount-points="^/(sys|proc|dev|host|etc)($$|/)"' volumes: prometheus_data: {}This compose file sets up three services:Prometheus: The main monitoring service.cAdvisor: For collecting container metrics.Node Exporter: For collecting host metrics.Step 2: Create Prometheus ConfigurationCreate a file named prometheus.yml with the following content:global: scrape_interval: 15sscrape_configs: - job_name: 'prometheus' static_configs: - targets: ['localhost:9090'] - job_name: 'cadvisor' static_configs: - targets: ['cadvisor:8080'] - job_name: 'node-exporter' static_configs: - targets: ['node-exporter:9100']This configuration file tells Prometheus where to scrape metrics from, including the Prometheus server itself.Step 3: Start the ServicesRun the following command to start the services:docker-compose up -dThis command will pull the necessary images and start the containers in detached mode.Setting Up Grafana for VisualizationNow that we have Prometheus collecting metrics, let's set up Grafana for visualization.Step 4: Add Grafana to Docker ComposeUpdate your docker-compose.yml file to include Grafana:grafana: image: grafana/grafana:latest container_name: grafana ports: - 3000:3000 volumes: - grafana_data:/var/lib/grafana environment: - GF_SECURITY_ADMIN_PASSWORD=adminvolumes: grafana_data: {}Step 5: Restart the ServicesRun the following command to apply the changes:docker-compose up -dStep 6: Configure GrafanaOpen a web browser and navigate to http://localhost:3000.Log in with the username admin and password admin.Go to Configuration > Data Sources.Add a new Prometheus data source.Set the URL to http://prometheus:9090.Click Save & Test.Step 7: Import DashboardsGrafana has many pre-built dashboards for Docker monitoring. You can import them using the following steps:Go to Create > Import.Enter the dashboard ID (e.g., 893 for Docker and system monitoring).Select your Prometheus data source.Click Import.These dashboards will provide graphs and visualizations for various metrics, including CPU and memory usage of your running containers.Prometheus Recording Rules: A Developer’s Guide to Query Optimization | Last9This guide breaks down how recording rules can help, with simple tips to improve performance and manage complex data.Book a DemoBook a DemoMonitoring Docker Containers in ProductionFor production environments, consider the following best practices:Use alerting: Set up Alertmanager to notify you of critical issues such as high resource usage or service downtimes.Implement security measures: Ensure proper authentication and encryption to secure your monitoring stack.Scale your monitoring: If your infrastructure grows, consider using remote storage solutions for long-term metric retention.Monitor the monitors: Keep an eye on the health of your monitoring tools themselves to ensure they are functioning properly.Monitoring Docker DaemonTo monitor the Docker daemon itself, you can use the Docker Engine metrics endpoint. Add the following to your prometheus.yml configuration file:- job_name: 'docker' static_configs: - targets: ['docker-host:9323']Make sure to replace docker-host with the appropriate IP address or hostname of your Docker host.Next, configure the Docker daemon to expose metrics by editing the /etc/docker/daemon.json file:{ "metrics-addr": "0.0.0.0:9323", "experimental": true}Restart the Docker daemon for these changes to take effect.High Availability in Prometheus: Best Practices and Tips | Last9This blog defines high availability in Prometheus, discusses challenges, and offers essential tips for reliable monitoring in cloud-native environments.Book a DemoBook a DemoAdvanced Monitoring TechniquesMonitoring Nginx with PrometheusIf you're running Nginx within your Docker environment, you can monitor it using the Nginx Prometheus Exporter. To set this up, add the following to your docker-compose.yml:nginx-exporter: image: nginx/nginx-prometheus-exporter:latest command: - '-nginx.scrape-uri=http://nginx:8080/stub_status' ports: - 9113:9113Then, add a new job to your prometheus.yml configuration file:- job_name: 'nginx' static_configs: - targets: ['nginx-exporter:9113']Kubernetes IntegrationIf you are using Kubernetes, you can adapt this monitoring setup by employing the Prometheus Operator, which automates the deployment and configuration of Prometheus in a Kubernetes cluster. The operator enables automatic discovery and monitoring of pods, services, and nodes within your cluster.Time Series Data and Backend StoragePrometheus is highly efficient in storing time series data, which allows for fast querying and analysis of metrics. However, for long-term storage, especially in larger environments, it is advisable to use remote storage solutions capable of handling extensive time series data.Automation and ProvisioningTo simplify and expedite the setup process, you can create scripts or utilize configuration management tools (e.g., Ansible or Terraform) to automate the deployment of your monitoring stack. This is especially useful when provisioning new environments or scaling your infrastructure.Plugins and ExtensionsGrafana supports a wide range of plugins that can extend its functionality. For example, the AWS CloudWatch plugin allows you to integrate metrics from AWS services alongside your Docker metrics, providing a comprehensive monitoring solution for hybrid environments.ConclusionMonitoring Docker containers with Prometheus and Grafana gives you valuable insights into the health and performance of your applications. As your infrastructure grows, it’s a good idea to revisit and fine-tune your monitoring setup to make sure everything runs smoothly. There are plenty of open-source projects on GitHub where you can explore different configurations and examples to suit your needs.Whether you’re running a small dev environment or managing a large production system, keeping an eye on your containers is key to maintaining reliability. If you have any questions or want to discuss this further, feel free to get in touch, or join our Discord community where developers like you are always sharing tips and advice.Good luck with your setup, and happy monitoring!FAQsHow do I monitor my Docker containers?You can monitor Docker containers by using tools like Prometheus and Grafana. Prometheus collects metrics from containers, while Grafana helps visualize them. Additionally, Docker’s built-in command-line tools like docker stats allow real-time resource monitoring of CPU, memory, and network usage.How do I use Prometheus and Grafana in Docker?To use Prometheus and Grafana in Docker, you can set them up using Docker Compose. Prometheus collects container metrics, while Grafana visualizes the data. Simply configure a docker-compose.yml file to include Prometheus, Grafana, and cAdvisor to gather container metrics.How do I monitor Docker containers in production?Monitoring Docker containers in production involves setting up Prometheus for metrics collection and using Alertmanager for notifications. Security and scalability are critical, so ensure secure authentication, and consider long-term storage for metrics. Remote storage options can help manage large datasets effectively.How do I monitor Docker daemon?To monitor the Docker daemon, you can expose Docker Engine metrics by configuring the Docker daemon to use the /metrics endpoint. Prometheus can then scrape these metrics by adding the Docker host's IP address and port to the Prometheus configuration file.What are the benefits of monitoring Docker containers?Monitoring Docker containers helps optimize performance, allocate resources, troubleshoot issues, plan for capacity, and ensure high availability. It provides insights into CPU, memory, and network usage, helping you maintain the health and performance of your applications.What is the difference between Docker monitoring and container monitoring?Docker monitoring specifically focuses on monitoring Docker containers and the Docker Engine, while container monitoring generally refers to tracking the performance of any containerized environment, regardless of the container runtime used, such as Docker, CRI-O, or containerd.How do I monitor a Docker container using Prometheus?You can monitor a Docker container using Prometheus by setting up cAdvisor or Node Exporter to gather metrics. Prometheus scrapes these metrics from your Docker environment, which can then be visualized in Grafana for better insights into container performance.SubscribeBook a Demo
Prometheus Rate Function: A Practical Guide to Using It | Last9
In this guide, we’ll walk you through the Prometheus rate function. You’ll discover how to analyze changes over time and use that information to enhance your monitoring strategy.
 Prometheus is a powerful and flexible tool for observability and monitoring, with the rate() function standing out as a key feature for tracking system behavior over time.This guide will walk you through how to use the rate() function effectively, covering its mechanics, use cases, and best practices to boost your monitoring and observability efforts, helping you build more reliable systems.Understanding the Prometheus Rate FunctionThe rate() function is a key component of PromQL (Prometheus Query Language) used for analyzing the rate of change in counter metrics over time. At its core, rate() calculates the per-second average rate of increase of time series in a range vector.rate() helps answer critical questions such as:"What is the current request rate for a service?""How rapidly is CPU usage increasing over a given time period?""What's the rate of errors occurring in our application?"These insights help in understanding system performance and behavior.The Importance of the Rate Function in MonitoringUnderstanding rates of change is crucial in monitoring systems for a few key reasons:Performance Monitoring: It helps identify sudden spikes or drops in system performance, allowing for quick detection of anomalies or potential issues.Capacity Planning: Analyzing trends in rates allows for predicting future resource needs and planning for scaling accordingly.Alerting: Rate-based alerts can catch issues before they become critical, enabling proactive problem-solving.SLO/SLA Tracking: Rates are often key components of service-level objectives and agreements, making them crucial for ensuring compliance and maintaining service quality.Trend Analysis: Rates provide valuable insights into long-term trends, helping in strategic decision-making and system optimization.Using the Rate Function: Syntax and Basic ExamplesThe basic syntax of the rate() function is straightforward:rate(metric[time_range])Example:Assume there's a counter metric, http_requests_total, which tracks the total number of HTTP requests to a service. To calculate the rate of requests per second over the last 5 minutes, use the following query:rate(http_requests_total[5m])This query returns the per-second rate of increase for http_requests_total over the last 5 minutes.Note: It's crucial to use rate() only counter-metrics. Applying it to gauge metrics will result in incorrect data.Prometheus Alternatives: Monitoring Tools You Should Know | Last9What are the alternatives to Prometheus? A guide to comparing different Prometheus Alternatives.Book a DemoReal-World Example: Monitoring API Request RatesLet's consider a scenario where you need to monitor request rates for different API endpoints. Here's how it can be set up:Instrument the API: Expose a counter metric, api_requests_total, with labels for the endpoint and method.Create a Grafana Dashboard: Use the following PromQL query to visualize the request rates:sum by (endpoint) (rate(api_requests_total{job="api-server"}[5m]))This query calculates the request rate for each endpoint over the last 5 minutes and sums up the rates for all methods.Set Up Alerts: Trigger an alert if the request rate for any endpoint exceeds 100 requests per second:sum by (endpoint) (rate(api_requests_total{job="api-server"}[5m])) > 100This setup provides a real-time view of API usage patterns, enabling quick identification of bottlenecks and helping optimize heavily used endpoints. Rate vs. Irate: When to Use EachPrometheus provides two similar functions, rate() and irate(), but they serve different purposes:rate() calculates the average rate of increase over the specified time range.irate() calculates the instant rate of increase using only the last two data points.When to Use Each:rate() is ideal for stable metrics and alerting, as it smooths out short-term fluctuations and gives you a more consistent view of the rate over time.irate() is better for graphing highly variable metrics, where you want to capture rapid changes and can tolerate more noise.# Stable rate over 5 minutesrate(http_requests_total[5m]) # Instant rate, more prone to spikesirate(http_requests_total[5m])Use rate() when you want a stable, long-term view of your metrics.Use irate() when you need to see short-term spikes or rapid changes.Advanced Usage: Combining rate() with Other FunctionsThe true potential of the rate() function in Prometheus comes when it’s combined with other PromQL functions. Below are a few advanced techniques to enhance your metrics analysis:1. Calculating Request Error RatesTo calculate the ratio of 5xx errors to total requests:sum(rate(http_requests_total{status=~"5.."}[5m])) / sum(rate(http_requests_total[5m]))This gives a clear view of your error rate by comparing 5xx errors to the total number of requests.2. Using histogram_quantile() with RatesTo calculate the 95th percentile of request durations over the last 5 minutes:histogram_quantile(0.95, sum by (le) (rate(http_request_duration_seconds_bucket[5m])))This is especially useful for tracking performance SLOs by providing a detailed view of latency.3. Smoothing Out Spikes with avg_over_time()To smooth out short-term fluctuations by averaging the request rate over a longer period:avg_over_time(rate(http_requests_total[5m])[1h:])This gives the average rate over the last hour, updated every 5 minutes, helping to track longer-term trends.4. Comparing Rates Across Different Time RangesTo detect sudden traffic spikes by comparing the short-term and long-term request rates:rate(http_requests_total[5m]) / rate(http_requests_total[1h]) > 1.2This query identifies when the short-term rate is 20% higher than the long-term rate.5. Calculating the Rate of Change for a Gauge MetricFor calculating the rate of change in gauge metrics (like memory usage) using deriv():deriv(process_resident_memory_bytes{job="app"}[1h])This tracks how quickly memory usage is changing over an hour.Optimizing Prometheus Remote Write Performance: Guide | Last9Master Prometheus remote write optimization. Learn queue tuning, cardinality management, and relabeling strategies to scale your monitoring infrastructure efficiently.Book a DemoCommon Pitfalls and How to Avoid ThemWhen working with the rate() function, keep an eye on these common issues:Too Short Time Ranges: Using a time range that's shorter than the scrape interval can result in inaccurate data. A good rule of thumb is to use a time range at least 4x the scrape interval. For instance, if your scrape interval is 15 seconds, set the time range in your rate() function to at least 1 minute.Ignoring Counter Resets: The rate() function can handle counter resets (e.g., when a service restarts), but these resets can still cause temporary spikes. Be mindful of this when interpreting data, as the rate is calculated from the available information.Misunderstanding Aggregation: Since rate() returns a per-second value, summing or averaging these rates won’t give an accurate total. Instead, sum the underlying counters and then apply the rate() function.Inappropriate Use with Gauges: The rate() function is specifically for counters. Using it with gauge metrics will yield incorrect results, so avoid this combination.Neglecting Label Changes: Frequent changes in label values can create gaps in your data, leading to inaccurate rate calculations. Always account for potential label changes when working with metrics.Best Practices for Using the rate() FunctionTo make the most of the rate() function in Prometheus, keep these best practices in mind:Choose the Right Time Range: Ensure the time range is long enough to capture meaningful trends while remaining short enough to respond to real-time changes.Alerting with Care: When using rate() in alerts, opt for longer time ranges to reduce the risk of false positives caused by short-term fluctuations.Leverage Other Functions: As highlighted in advanced examples, combining rate() with other PromQL functions can provide richer insights into your data.Know Your Metrics: Understand the nature of your data—such as how often metrics update and their variability—to ensure accurate monitoring.Test Thoroughly: Validate your queries with historical data to ensure they're reliable under different conditions and scenarios.ConclusionThe Prometheus rate() function is a fundamental tool for monitoring, offering versatility from tracking request rates to analyzing performance and error metrics. Its strength lies in revealing the rate of change across various metrics, making it vital for any observability strategy.To truly master the rate() function, practice is key. Experimenting with different queries and time ranges can uncover the best approaches for your specific use cases. As systems grow in complexity, proficiency with functions like rate() becomes essential to ensure smooth performance, reliability, and a positive user experience.FAQs Q: How does the Prometheus rate() function differ from increase()?A: While rate() calculates the per-second average rate of increase, increase() calculates the total increase in the counter's value over the time range. rate() is generally more useful for ongoing monitoring, while increase() can help understand total change over a specific period.Q: How do you calculate request rates using the Prometheus rate function?A: To calculate request rates, use a query like rate(http_requests_total[5m]). This will give the per-second rate of requests over the last 5 minutes. These rates can be summed or grouped as needed, e.g., sum(rate(http_requests_total[5m])) for the total request rate across all instances.Q: Are there approaches for capturing spikes with PromQL?A: Yes, max_over_time() can be used with rate() to capture spikes. For example, max_over_time(rate(http_requests_total[5m])[1h:]) will show the maximum rate observed in 5-minute windows over the last hour.Q: How do you calculate the increase of a counter over time using Prometheus functions?A: To calculate the total increase of a counter, use the increase() function. For example, increase(http_requests_total[1h]) will show the total increase in the number of requests over the last hour.Q: Can rate() be used with all types of Prometheus metrics?A: No, rate() should only be used with counter-metrics. It doesn't make sense to use rate() with gauge metrics, as they don't represent cumulative values.SubscribeBook a Demo
Prometheus is a powerful and flexible tool for observability and monitoring, with the rate() function standing out as a key feature for tracking system behavior over time.This guide will walk you through how to use the rate() function effectively, covering its mechanics, use cases, and best practices to boost your monitoring and observability efforts, helping you build more reliable systems.Understanding the Prometheus Rate FunctionThe rate() function is a key component of PromQL (Prometheus Query Language) used for analyzing the rate of change in counter metrics over time. At its core, rate() calculates the per-second average rate of increase of time series in a range vector.rate() helps answer critical questions such as:"What is the current request rate for a service?""How rapidly is CPU usage increasing over a given time period?""What's the rate of errors occurring in our application?"These insights help in understanding system performance and behavior.The Importance of the Rate Function in MonitoringUnderstanding rates of change is crucial in monitoring systems for a few key reasons:Performance Monitoring: It helps identify sudden spikes or drops in system performance, allowing for quick detection of anomalies or potential issues.Capacity Planning: Analyzing trends in rates allows for predicting future resource needs and planning for scaling accordingly.Alerting: Rate-based alerts can catch issues before they become critical, enabling proactive problem-solving.SLO/SLA Tracking: Rates are often key components of service-level objectives and agreements, making them crucial for ensuring compliance and maintaining service quality.Trend Analysis: Rates provide valuable insights into long-term trends, helping in strategic decision-making and system optimization.Using the Rate Function: Syntax and Basic ExamplesThe basic syntax of the rate() function is straightforward:rate(metric[time_range])Example:Assume there's a counter metric, http_requests_total, which tracks the total number of HTTP requests to a service. To calculate the rate of requests per second over the last 5 minutes, use the following query:rate(http_requests_total[5m])This query returns the per-second rate of increase for http_requests_total over the last 5 minutes.Note: It's crucial to use rate() only counter-metrics. Applying it to gauge metrics will result in incorrect data.Prometheus Alternatives: Monitoring Tools You Should Know | Last9What are the alternatives to Prometheus? A guide to comparing different Prometheus Alternatives.Book a DemoReal-World Example: Monitoring API Request RatesLet's consider a scenario where you need to monitor request rates for different API endpoints. Here's how it can be set up:Instrument the API: Expose a counter metric, api_requests_total, with labels for the endpoint and method.Create a Grafana Dashboard: Use the following PromQL query to visualize the request rates:sum by (endpoint) (rate(api_requests_total{job="api-server"}[5m]))This query calculates the request rate for each endpoint over the last 5 minutes and sums up the rates for all methods.Set Up Alerts: Trigger an alert if the request rate for any endpoint exceeds 100 requests per second:sum by (endpoint) (rate(api_requests_total{job="api-server"}[5m])) > 100This setup provides a real-time view of API usage patterns, enabling quick identification of bottlenecks and helping optimize heavily used endpoints. Rate vs. Irate: When to Use EachPrometheus provides two similar functions, rate() and irate(), but they serve different purposes:rate() calculates the average rate of increase over the specified time range.irate() calculates the instant rate of increase using only the last two data points.When to Use Each:rate() is ideal for stable metrics and alerting, as it smooths out short-term fluctuations and gives you a more consistent view of the rate over time.irate() is better for graphing highly variable metrics, where you want to capture rapid changes and can tolerate more noise.# Stable rate over 5 minutesrate(http_requests_total[5m]) # Instant rate, more prone to spikesirate(http_requests_total[5m])Use rate() when you want a stable, long-term view of your metrics.Use irate() when you need to see short-term spikes or rapid changes.Advanced Usage: Combining rate() with Other FunctionsThe true potential of the rate() function in Prometheus comes when it’s combined with other PromQL functions. Below are a few advanced techniques to enhance your metrics analysis:1. Calculating Request Error RatesTo calculate the ratio of 5xx errors to total requests:sum(rate(http_requests_total{status=~"5.."}[5m])) / sum(rate(http_requests_total[5m]))This gives a clear view of your error rate by comparing 5xx errors to the total number of requests.2. Using histogram_quantile() with RatesTo calculate the 95th percentile of request durations over the last 5 minutes:histogram_quantile(0.95, sum by (le) (rate(http_request_duration_seconds_bucket[5m])))This is especially useful for tracking performance SLOs by providing a detailed view of latency.3. Smoothing Out Spikes with avg_over_time()To smooth out short-term fluctuations by averaging the request rate over a longer period:avg_over_time(rate(http_requests_total[5m])[1h:])This gives the average rate over the last hour, updated every 5 minutes, helping to track longer-term trends.4. Comparing Rates Across Different Time RangesTo detect sudden traffic spikes by comparing the short-term and long-term request rates:rate(http_requests_total[5m]) / rate(http_requests_total[1h]) > 1.2This query identifies when the short-term rate is 20% higher than the long-term rate.5. Calculating the Rate of Change for a Gauge MetricFor calculating the rate of change in gauge metrics (like memory usage) using deriv():deriv(process_resident_memory_bytes{job="app"}[1h])This tracks how quickly memory usage is changing over an hour.Optimizing Prometheus Remote Write Performance: Guide | Last9Master Prometheus remote write optimization. Learn queue tuning, cardinality management, and relabeling strategies to scale your monitoring infrastructure efficiently.Book a DemoCommon Pitfalls and How to Avoid ThemWhen working with the rate() function, keep an eye on these common issues:Too Short Time Ranges: Using a time range that's shorter than the scrape interval can result in inaccurate data. A good rule of thumb is to use a time range at least 4x the scrape interval. For instance, if your scrape interval is 15 seconds, set the time range in your rate() function to at least 1 minute.Ignoring Counter Resets: The rate() function can handle counter resets (e.g., when a service restarts), but these resets can still cause temporary spikes. Be mindful of this when interpreting data, as the rate is calculated from the available information.Misunderstanding Aggregation: Since rate() returns a per-second value, summing or averaging these rates won’t give an accurate total. Instead, sum the underlying counters and then apply the rate() function.Inappropriate Use with Gauges: The rate() function is specifically for counters. Using it with gauge metrics will yield incorrect results, so avoid this combination.Neglecting Label Changes: Frequent changes in label values can create gaps in your data, leading to inaccurate rate calculations. Always account for potential label changes when working with metrics.Best Practices for Using the rate() FunctionTo make the most of the rate() function in Prometheus, keep these best practices in mind:Choose the Right Time Range: Ensure the time range is long enough to capture meaningful trends while remaining short enough to respond to real-time changes.Alerting with Care: When using rate() in alerts, opt for longer time ranges to reduce the risk of false positives caused by short-term fluctuations.Leverage Other Functions: As highlighted in advanced examples, combining rate() with other PromQL functions can provide richer insights into your data.Know Your Metrics: Understand the nature of your data—such as how often metrics update and their variability—to ensure accurate monitoring.Test Thoroughly: Validate your queries with historical data to ensure they're reliable under different conditions and scenarios.ConclusionThe Prometheus rate() function is a fundamental tool for monitoring, offering versatility from tracking request rates to analyzing performance and error metrics. Its strength lies in revealing the rate of change across various metrics, making it vital for any observability strategy.To truly master the rate() function, practice is key. Experimenting with different queries and time ranges can uncover the best approaches for your specific use cases. As systems grow in complexity, proficiency with functions like rate() becomes essential to ensure smooth performance, reliability, and a positive user experience.FAQs Q: How does the Prometheus rate() function differ from increase()?A: While rate() calculates the per-second average rate of increase, increase() calculates the total increase in the counter's value over the time range. rate() is generally more useful for ongoing monitoring, while increase() can help understand total change over a specific period.Q: How do you calculate request rates using the Prometheus rate function?A: To calculate request rates, use a query like rate(http_requests_total[5m]). This will give the per-second rate of requests over the last 5 minutes. These rates can be summed or grouped as needed, e.g., sum(rate(http_requests_total[5m])) for the total request rate across all instances.Q: Are there approaches for capturing spikes with PromQL?A: Yes, max_over_time() can be used with rate() to capture spikes. For example, max_over_time(rate(http_requests_total[5m])[1h:]) will show the maximum rate observed in 5-minute windows over the last hour.Q: How do you calculate the increase of a counter over time using Prometheus functions?A: To calculate the total increase of a counter, use the increase() function. For example, increase(http_requests_total[1h]) will show the total increase in the number of requests over the last hour.Q: Can rate() be used with all types of Prometheus metrics?A: No, rate() should only be used with counter-metrics. It doesn't make sense to use rate() with gauge metrics, as they don't represent cumulative values.SubscribeBook a Demo
Last9 on Flipboard
Last9 (@LastNine) on Flipboard
Follow LastNine to see stories curated to collections like Last9 of Reliability on Flipboard.
 Flipboard
Flipboard
SRE Stories
SRE Story with Iris Dyrmishi
OpenTelemetry and building Observability Platforms
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
The SRE Experience: Isaac on Automation, Challenges, and Mentoring
SRE Experience, Automation and Challenges
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
Salim’s Insights from 21+ Years of SRE at Google
The Evolution of SRE and Today’s Observability Challenges
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
Dan Slimmon’s SRE Lessons from the Frontlines
A Candid Chat on Resilience, Team Communication and Observability
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Sunny Arora
Internship to contributing to Core Distributed Tracing Platform at Razorpay with Sunny Arora
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Alex Hidalgo
Becoming better SRE by understanding the human connection with software systems
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Srinivas Devaki
From Frontend to SRE to building a product for SREs
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Ricardo Castro
Applying Software Engineering principles to world of Operations
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Michael Hausenblas
Community, Empathy and OpenTelemetry
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Iris Dyrmishi
OpenTelemetry and building Observability Platforms
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Matthew Iselin
Sys-Admin Down Under to SRE Manager in Bay Area with Matthew Iselin from Replit
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
A Day in the life of an SRE | Sagar Rakshe
Turbo C to SRE via startups, consulting and again startup with Sagar Rakshe
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
SRE Story with Sathya Bhat
Learnings, musings, taking your chances and much more with Sathya Bhat
 SRE StoriesSathya Bhat
SRE StoriesSathya Bhat
A day in the life of an SRE | Sebastian Vietz
Today, we have Sebastian Vietz from Compass Digital sharing his SRE story. I came across Sebastian’s post on LinkedIn a few weeks back that he will be coming to SRECon and connected with him. Meeting him in person and seeing his enthusiasm and energy about observability and reliability engineering w…
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
A Day in the Life of an SRE | Tiago Dias Generoso
Tiago Dias Generoso from Brasil sharing his #SRE Story.
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
A day in the life of an SRE | Suraj Nath
Today we have Suraj Nath as part of the SRE Stories. Suraj works as Software Engineer at Grafana Labs on Tempo and Grafana Cloud Traces products. Before this, he was an early hire at Clarisights. Suraj is a speaker at various technical conferences. He also runs a meetup -
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
A day in the life of an SRE | Mohit Shukla
For the second edition of the A day in the life of an SRE series, we have Mohit Shukla. Mohit is known as ethicalmohit on interwebs. He works as a Site Reliability Engineer at Bureau, Inc. Mohit introduces himself as an SRE generalist with seven years of experience. He has worked on multi-dimensions…
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
A day in the life of an SRE | Ashwin Murali
A day in the life of an SRE | Ashwin Murali - Cloud Infra and Engineering Manager at CoLearn
 SRE StoriesPrathamesh Sonpatki
SRE StoriesPrathamesh Sonpatki
On Medium -
Laffer’s Curve and Reliability of Software Systems
In the world of economics, the Laffer Curve is a concept that depicts the relationship between tax rates and government revenue. However, this curve can also be applied to various domains beyond…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
Are you following the SRE way?
Site Reliability Engineering (SRE) is an established and critical practice, widely recognized for its importance in modern software organizations. Its emphasis on reliability, scalability, and…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
Anatomy of Metrics
1. Metric Name: This is the unique identifier for each type of data that is being collected. The name should be descriptive enough to represent the information being tracked. 2. Timestamp: This is…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
The Fallacies of Distributed Systems
In the realm of computer science, distributed systems have revolutionized how we perceive, manage, and employ data processing. A distributed system brings together multiple computer nodes…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
Metrics vs. Logs: A Detailed Exploration
In the complex landscape of modern computing, two key concepts reign supreme: metrics and logs. While both are instrumental in understanding the performance and operation of software applications…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
A day in the life of an SRE
I always look forward to hearing stories from people, their workflows, and how they improve their craft. As part of Last9, where we build…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki
Starting o11y.wiki
When I joined Last9 three years back, I knew little about SRE and Observability. The situation is not changed after three years :) There is a lot to learn in the Observability space. I am yet to find…
 MediumPrathamesh Sonpatki
MediumPrathamesh Sonpatki